Vulnerable—Win2k3
一、主机发现及端口扫描
由于开机的时候已经发现这是一个 Windows Server 2003 的环境了,Windows 系列主机又是禁止 Ping 扫描的,所以使用 ARP 扫描来进行主机发现
root@kali:~/Desktop/valecalida's_Sript# python3 ARP_Scan.py -i eth0 10.87.51.0/24
[..] 开始进行ARP扫描
IP: 10.87.51.1
IP: 10.87.51.2
IP: 10.87.51.18
IP: 10.87.51.254
[+] 本次扫描共花费 2.5348236560821533 秒去除 1、2、254 剩下的只有一个 18 ,也就是本次需要测试的目标主机:10.87.51.18 。
root@kali:~# nmap -A -p- 10.87.51.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-25 02:13 EDT
Nmap scan report for 10.87.51.18
Host is up (0.00081s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
1433/tcp open ms-sql-s Microsoft SQL Server 2005 9.00.1399.00; RTM
| ms-sql-ntlm-info:
|_ Product_Version: 5.2.3790
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2019-01-27T19:20:39
|_Not valid after: 2049-01-27T19:20:39
|_ssl-date: 2019-01-27T04:42:17+00:00; -1y89d01h36m05s from scanner time.
27689/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Error
MAC Address: 00:0C:29:75:04:1D (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Microsoft Windows 2003|XP
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_xp::sp2
OS details: Microsoft Windows Server 2003 SP1 - SP2, Microsoft Windows XP SP2 or Windows Server 2003 SP2
Network Distance: 1 hop
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -454d01h36m05s
| ms-sql-info:
| 10.87.51.18:1433:
| Version:
| name: Microsoft SQL Server 2005 RTM
| number: 9.00.1399.00
| Product: Microsoft SQL Server 2005
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
TRACEROUTE
HOP RTT ADDRESS
1 0.81 ms 10.87.51.18二、渗透测试流程
经过上面的扫描,发现该靶机开放了 1433 跟 27689 这两个端口,这两个端口对应的服务如下:
1433 Microsoft SQL Server 5.2.3790
27689 Microsoft IIS httpd 6.0使用 dirb 对站点的目录进行一下扫描:
root@kali:~# dirb http://10.87.51.18:27689
==> DIRECTORY: http://10.87.51.18:27689/admin/
==> DIRECTORY: http://10.87.51.18:27689/Admin/
==> DIRECTORY: http://10.87.51.18:27689/ADMIN/
+ http://10.87.51.18:27689/aspnet_client (CODE:403|SIZE:218)
==> DIRECTORY: http://10.87.51.18:27689/css/
==> DIRECTORY: http://10.87.51.18:27689/images/
==> DIRECTORY: http://10.87.51.18:27689/Images/
==> DIRECTORY: http://10.87.51.18:27689/js/
+ http://10.87.51.18:27689/robots.txt (CODE:200|SIZE:60)
==> DIRECTORY: http://10.87.51.18:27689/user/
+ http://10.87.51.18:27689/web.config (CODE:500|SIZE:4507先查看一下最容易包含信息的 robots.txt :
User-agent: *
Disallow:
/Default.aspx
/admin/
/upfile/可以看到,不允许爬取的目录有 /admin/ 和 /upfile/ ,经过查看发现,两个目录都无法访问
另外还有一个 /Default.aspx ,看一下这个文件
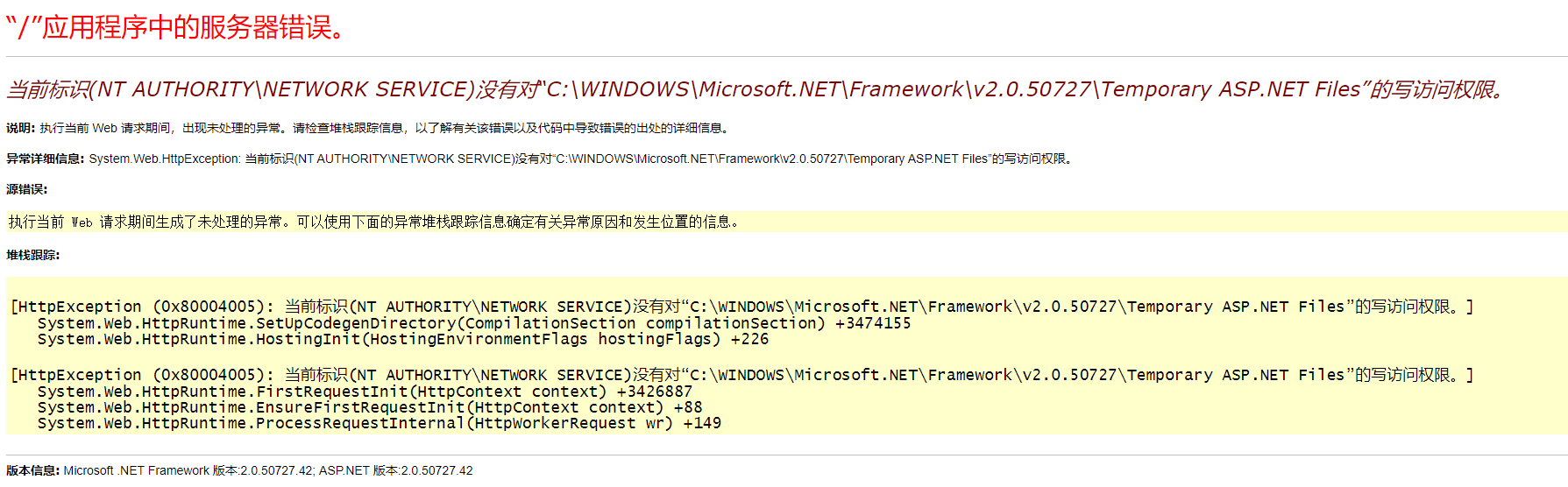
已经知道该靶机用的是 IIS 结构,所以使用 nikto 扫描一下
root@kali:~# nikto -h 10.87.51.18:27689
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.87.51.18
+ Target Hostname: 10.87.51.18
+ Target Port: 27689
+ Start Time: 2020-04-25 05:24:55 (GMT-4)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/6.0
+ Retrieved x-powered-by header: ASP.NET
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-aspnet-version header: 2.0.50727
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST
+ OSVDB-3092: /web.config.bak: ASP config backup file is accessible.
+ 7917 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2020-04-25 05:25:43 (GMT-4) (48 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested得到了文件 /web.config.bak ,下载查看文件内容
<?xml version="1.0"?>
<configuration>
<appSettings>
<add key="DBConnectionString" value="server=127.0.0.1;database=FileManage;User Id=down;pwd=downsql" />
</appSettings>
<system.web>
<!--
设置 compilation debug="true" 将调试符号插入
已编译的页面中。但由于这会
影响性能,因此只在开发过程中将此值
设置为 true。
-->
<compilation debug="true"/>
<!--
通过 <authentication> 节可以配置 ASP.NET 使用的
安全身份验证模式,
以标识传入的用户。
-->
<authentication mode="Windows"/>
<!--
如果在执行请求的过程中出现未处理的错误,
则通过 <customErrors> 节可以配置相应的处理步骤。具体说来,
开发人员通过该节可以配置
要显示的 html 错误页
以代替错误堆栈跟踪。
<customErrors mode="off" defaultRedirect="GenericErrorPage.htm">
<error statusCode="403" redirect="NoAccess.htm" />
<error statusCode="404" redirect="FileNotFound.htm" />
</customErrors>
-->
<customErrors mode="Off"/>
</system.web>
</configuration>
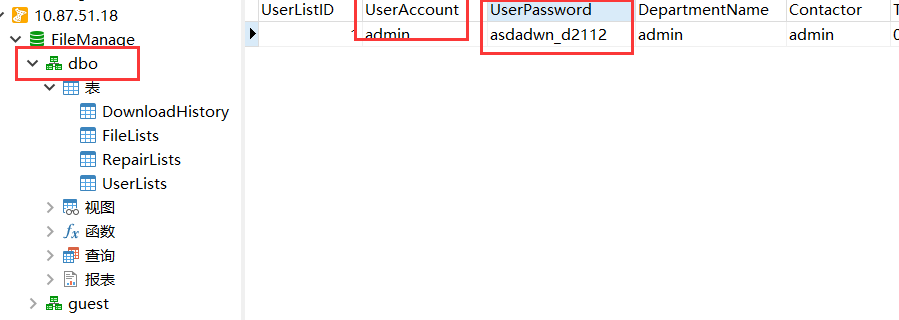
得到了连接 mssql 的用户名与密码:admin,asdadwn_d2112
 “>
“>
本来靶机是有三个考点的,但是由于靶机出现了问题,所以本次测试到此为止…

